A study codenamed “SAPwned” has uncovered serious vulnerabilities in the SAP AI Core system, which allowed attackers to gain access to clients’ cloud environments and their confidential data.
Stages of the Attack
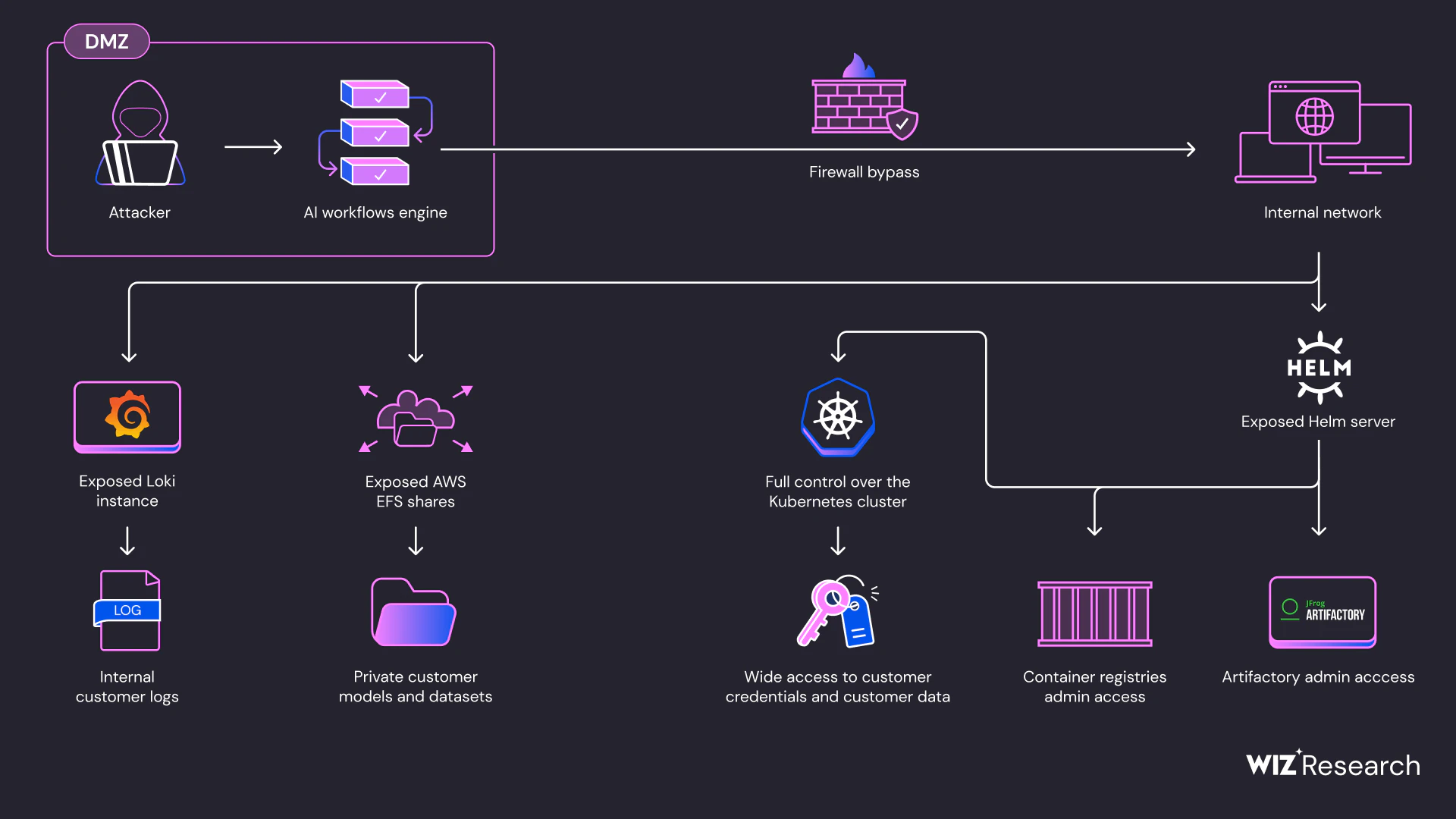
The primary cause of the identified issues was the ability to execute malicious AI models and training procedures, which essentially function as code. Despite protective measures, two configuration parameters overlooked by the SAP admission controller enabled attackers to obtain the Istiod cluster token and circumvent network restrictions.
The attackers were able to request and retrieve the Loki configuration via the /config path, leading to the leakage of AWS secrets necessary for system access. Additionally, large volumes of AI data, including code and training datasets sorted by client ID, were exposed through instances of AWS Elastic File System (EFS).
Compromise of Internal Systems
Internal systems such as the Docker Registry and Artifactory were also compromised through an unauthenticated Helm server. This allowed attackers to view internal builds and images, potentially leading to the leakage of client data and trade secrets. There was also a threat to the supply chain of SAP AI Core, as attackers could alter builds and images using the provided write access.
Furthermore, the unauthorized Helm server exposed Google access tokens and client confidential information, further increasing the risk of system compromise. The SAP access key provided additional attack opportunities, extending read and write access.
Security Measures
SAP acknowledged the existence of the vulnerabilities and stated that they have all been addressed by the company’s security team. The company assured that there was no compromise of client information. The impact of the attack could have been mitigated by strengthening internal services, which would have reduced the severity of the incident from a complete service takeover to minor security issues.
Future Preventative Measures
In the future, it is imperative to establish robust barriers to prevent the execution of untrusted code in the same environment as other clients and internal resources.


