At the Black Hat 2024 conference, currently taking place in Las Vegas (August 7-8), security researcher Alon Leviev from SafeBreach unveiled two new zero-day vulnerabilities that could be exploited in so-called Downgrade attacks to roll back Windows 10, 11, and Server operating systems to older versions, thereby enabling the exploitation of previously patched security flaws.
Naturally, Leviev adhered to a policy of responsible disclosure and notified Microsoft of the vulnerabilities in advance. However, the flaws, identified as CVE-2024-38202 and CVE-2024-21302, have yet to be patched, though the company has provided certain mitigation recommendations.
Downgrade attacks allow attackers to force an updated device to revert to older software versions, reintroducing previous security flaws that could be exploited to compromise the system.
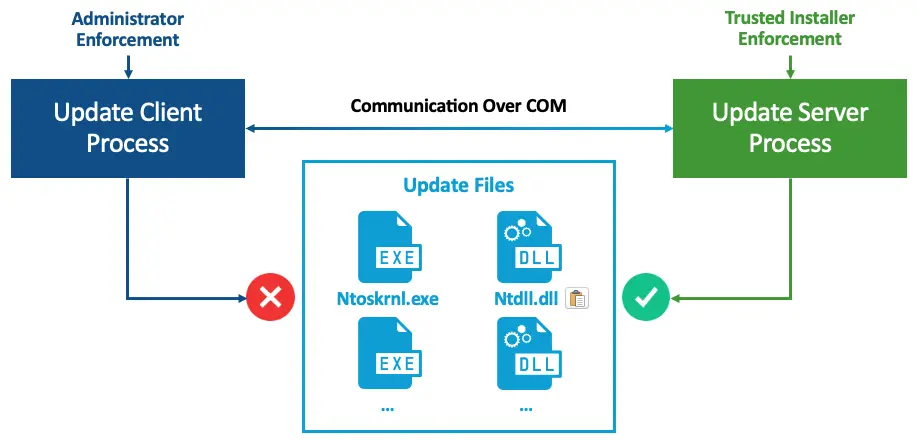
Leviev discovered that the Windows update process could be compromised to downgrade critical OS components, such as DLL libraries and the NT kernel. Even though these components would effectively be outdated after the attack, Windows Update would still report that the system is fully up-to-date, and recovery and scanning tools would not detect any issues.
Leviev also uncovered methods to disable Windows Virtualization-Based Security (VBS), including Credential Guard and Hypervisor-Protected Code Integrity (HVCI), even when using UEFI records. According to the researcher, this is the first instance of bypassing UEFI records without physical access to the device.
The expert noted that this type of attack is undetected by Endpoint Detection and Response (EDR) solutions and invisible to Windows Update, making it particularly dangerous. Leviev emphasized that the vulnerability renders the term “fully updated” meaningless for any Windows machine, exposing it to thousands of previously fixed vulnerabilities.
Leviev introduced the attack, dubbed “Windows Downdate,” six months after reporting the vulnerabilities to Microsoft. The company confirmed that it is working on fixes, but no working patch has been released yet.
Microsoft stated that it is unaware of any attempts to exploit these vulnerabilities in the wild and recommended following the guidelines published in two security advisories to mitigate the risk until the update is released.
Leviev pointed out that the implications of these vulnerabilities are significant not only for Windows but also for other operating systems that may be susceptible to similar downgrade attacks.
Microsoft representatives thanked SafeBreach for identifying and responsibly disclosing the vulnerability. The company is working on developing countermeasures to protect against these risks, including the creation of an update that will recall outdated, unsecured Virtualization Based Security (VBS) system files. However, the testing process for the update will take time due to the large number of affected files.


