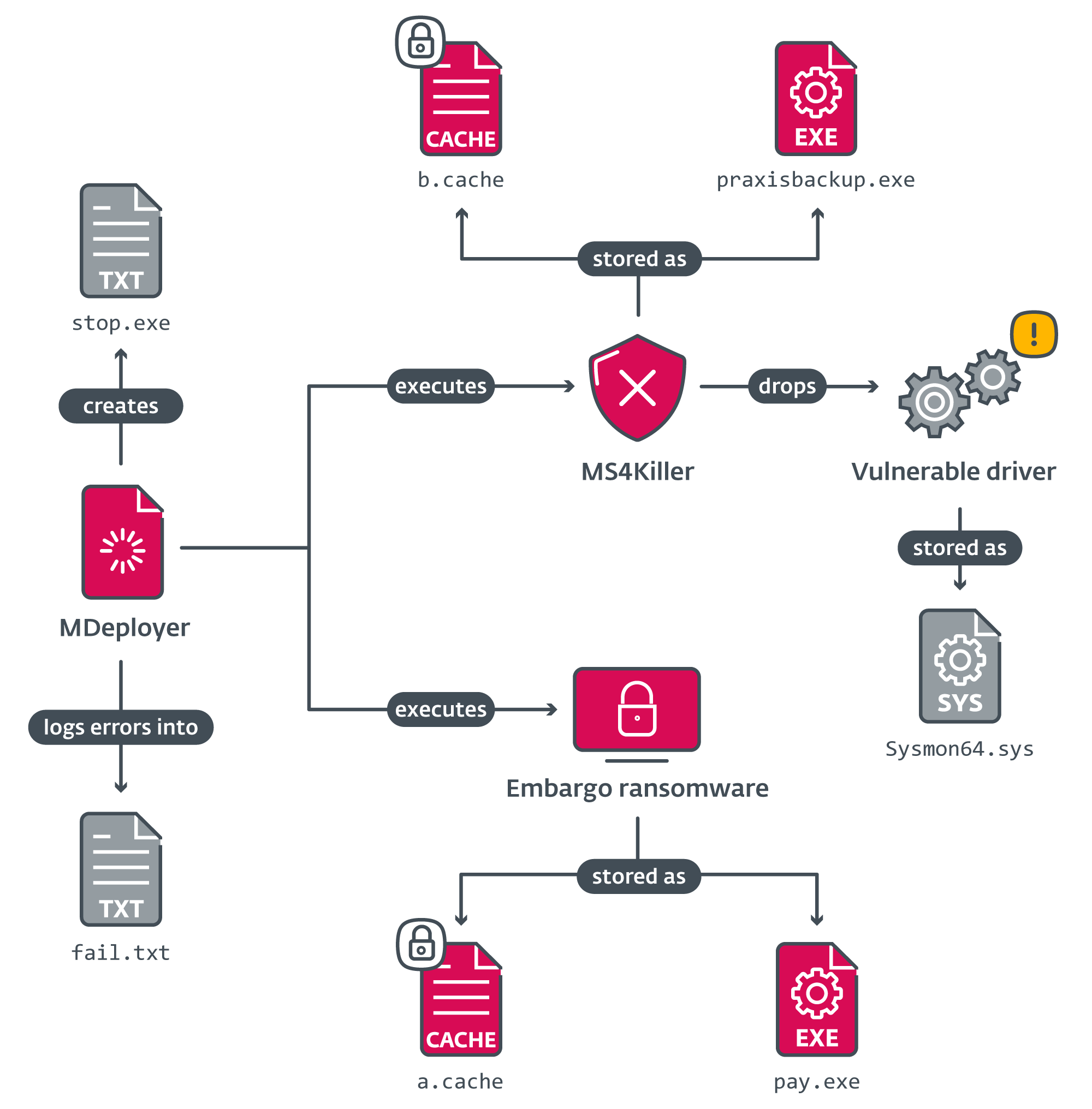
Researchers from ESET have uncovered new malware crafted by the Embargo group for deploying its namesake ransomware. Written in Rust, Embargo’s tools enable the creation of versatile cross-platform attack mechanisms targeting both Windows and Linux systems. The toolkit comprises the MDeployer loader and the MS4Killer security-disabling program, each customized per target, enhancing the efficacy of bypassing defensive systems. Notably, MS4Killer is compiled uniquely for each target and zeroes in on specific security frameworks, facilitating access to corporate data.
The Embargo group first captured ESET’s attention in June 2024, though its public mention surfaced in May of the same year. Experts note that the group’s toolkit remains a work in progress; each attack reveals unique versions and leaves artifacts indicating ongoing development efforts. The first incidents in the U.S. occurred in July 2024, where updated versions of MDeployer and MS4Killer were used in corporate networks. During these attacks, MDeployer versions were repeatedly modified mid-operation, likely as real-time adjustments following initial failures.
MDeployer serves as the primary tool, launching both MS4Killer and the Embargo ransomware itself. During operation, MDeployer decrypts two files—a.cache and b.cache—and uses them to execute malicious code. MS4Killer runs continuously as MDeployer completes the attack, erasing traces, deleting files, and rebooting the system. Of particular note is the group’s tactic of leveraging Windows Safe Mode to disable security solutions that are inactive in this mode, simplifying the attack’s execution.
Embargo distinguishes itself through a “double extortion” technique: should the victim refuse to pay, stolen data is published on a leak site. The group engages with victims via its infrastructure and the Tox messenger, exerting additional pressure to secure compliance. Analysts believe Embargo operates as a RaaS (ransomware as a service) provider, offering cyberattack tools to other criminals, with affiliates receiving a share based on successful outcomes. In the wake of recent arrests and dismantling of other prominent groups like BlackCat and LockBit, Embargo has carved out its niche, offering a more adaptable and efficient approach.
ESET’s analysis also revealed that Embargo’s tools contain bugs and logical errors. For example, one MDeployer version mistakenly deleted its payload file before attempting to execute it, causing malfunctions. Such errors explain the presence of multiple tool versions within a single attack, as the group adjusts tools on the fly.
MS4Killer stands out for employing the BYOVD (Bring Your Own Vulnerable Driver) technique, whereby vulnerable drivers terminate security processes. It continuously monitors and terminates security processes using the vulnerable driver probmon.sys, allowing attackers to circumvent kernel-level defenses. MS4Killer also obfuscates its actions with XOR encryption for strings and leverages the Rayon parallelism library to distribute process-termination tasks across separate threads, enhancing attack efficiency.
Embargo’s meticulous customization of its tools underscores its high level of preparation and substantial resources.


