Cybersecurity researchers have issued a warning about a new wave of phishing attacks orchestrated through a Phishing-as-a-Service (PhaaS) platform known as Rockstar 2FA. These attacks are designed to steal Microsoft 365 user credentials, including session cookies.
A recent report from Trustwave highlights that this operation employs an “adversary-in-the-middle” (AiTM) technique, enabling attackers to intercept credentials and session cookies even when multi-factor authentication (MFA) is enabled.
Rockstar 2FA is considered an evolved version of the DadSec toolkit, also known as Phoenix. Microsoft monitors the developers and distributors of this platform under the codename Storm-1575. Offered as a subscription service, the toolkit costs $200 for two weeks or $350 for a month, empowering cybercriminals with limited technical expertise to launch large-scale attacks.
Key features of Rockstar 2FA include bypassing two-factor authentication, cookie harvesting, anti-bot protection, customizable login page themes imitating popular services, and integration with Telegram bots. The platform also provides a user-friendly administrative dashboard for managing malicious campaigns and personalizing phishing links.
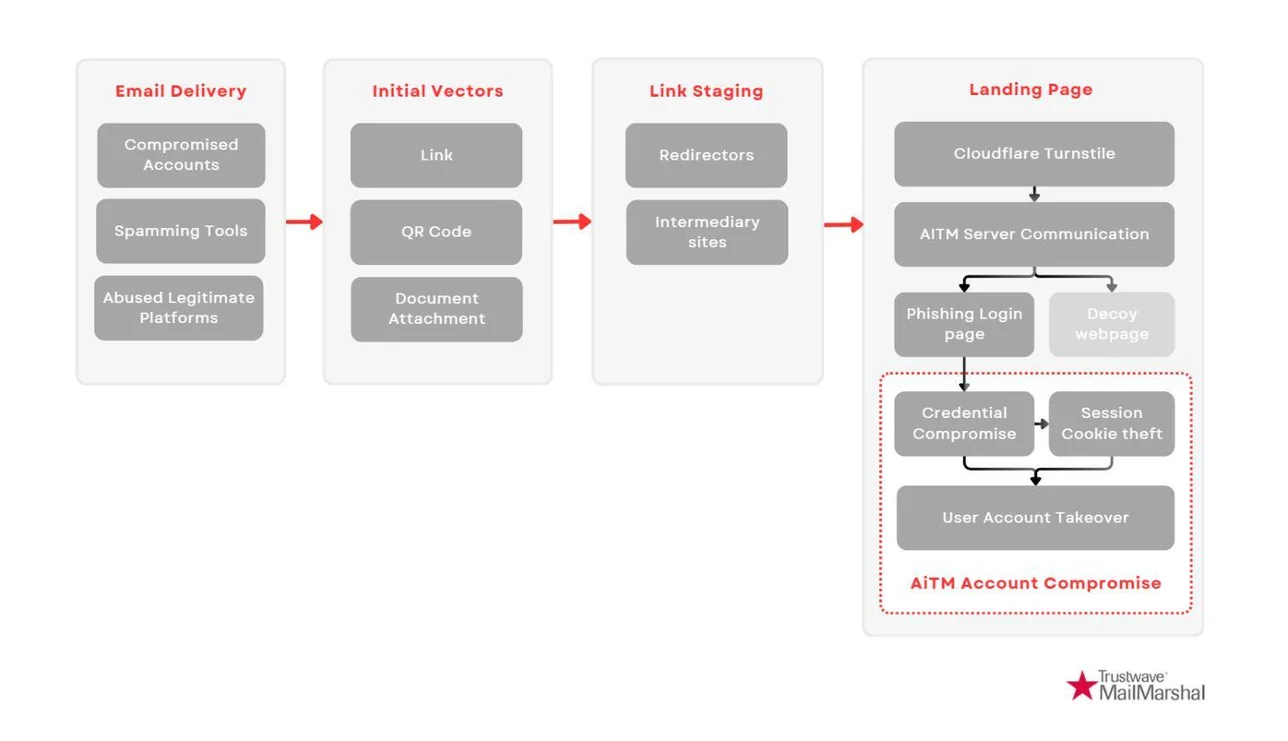
Cybercriminals employ various methods to gain initial access, including URLs, QR codes, and email attachments. These phishing messages often originate from already compromised accounts or spam tools. To evade anti-spam filters, attackers utilize legitimate link-shortening services, redirects, and Cloudflare Turnstile for protection.
Trustwave reports that phishing links are frequently hosted on trusted platforms such as Google Docs Viewer, Atlassian Confluence, and Microsoft OneDrive. This tactic enhances the attack’s credibility, as users are less likely to question the legitimacy of links originating from such well-known sources.
Data entered by victims on fraudulent pages is instantly transmitted to the attackers’ servers. The stolen credentials are then used to retrieve session cookies, granting full access to accounts while bypassing multi-factor authentication.
The rise of cybercrime as a service underscores how the technological accessibility and user-friendly nature of malicious tools pose a significant threat, even in the hands of inexperienced hackers. To mitigate such risks, users must remain vigilant when interacting with online resources, regardless of how trustworthy they appear.


