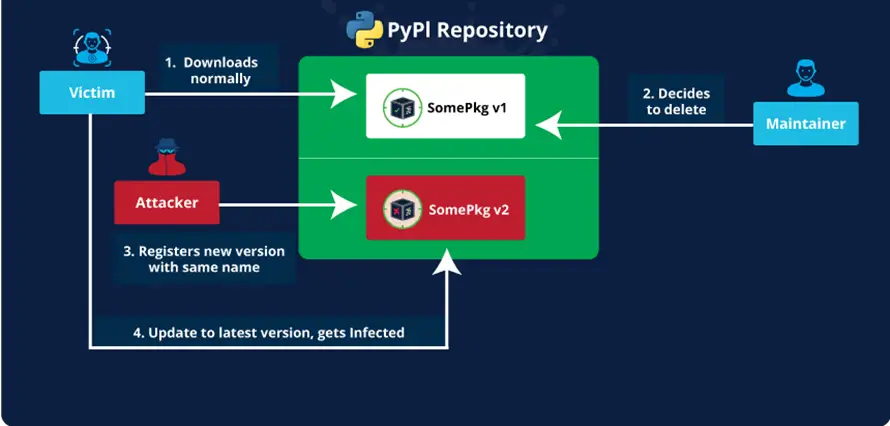
The JFrog team has uncovered a new method of supply chain attacks that was employed against PyPI packages. The technique, dubbed “Revival Hijack,” exploits the ability to re-register deleted packages. The attack occurs when a package is removed from the platform, its name becomes available for registration by other users, allowing malicious actors to hijack popular packages and disseminate malware.
The research revealed that this method could potentially hijack around 22,000 existing packages, leading to hundreds of thousands of downloads of malicious versions. However, JFrog managed to avert significant damage before cybercriminals could exploit the vulnerability on a large scale.
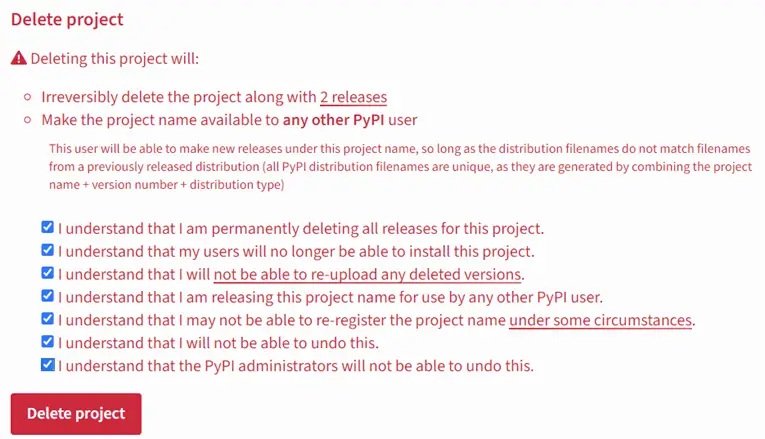
In the case of PyPI, one of the platform’s most vulnerable aspects is its package deletion policy. Once a project is removed, its name immediately becomes available for re-registration, without users receiving any warnings about the package’s deletion. This mechanism makes the Revival Hijack method particularly dangerous, as users may update what were once safe packages, unaware that they have been compromised by attackers.
One such example is the “pingdomv3” package, which was hijacked and used to spread malicious code. After taking control of the package, hackers inserted malicious code that executed during the installation or update of the package. However, the code was swiftly identified and removed.
During an experiment, the JFrog team tested this method by creating test packages and reclaiming them after deletion. The results showed that the PyPI system does not recognize changes in package ownership, enabling attackers to easily replace deleted versions with their own, without triggering any warnings during updates.
To mitigate these attacks, the JFrog team reserved over 22,000 packages using a dedicated account, uploading safe, empty versions of the packages. This measure protected the PyPI community from the threats associated with this type of attack. Nevertheless, the team emphasizes that users must remain vigilant and avoid installing packages that have been deleted to minimize risk.


