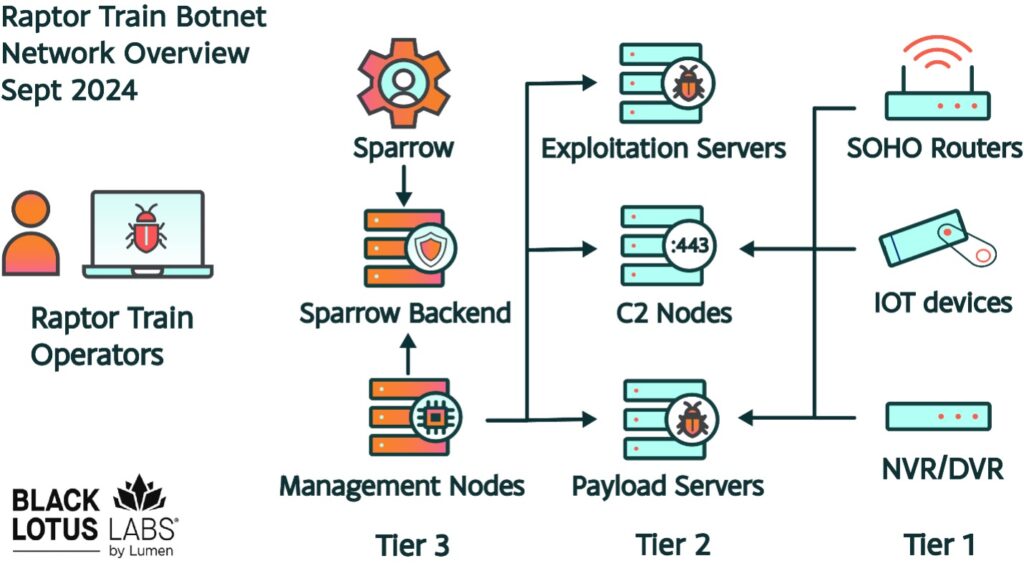
Overview of the Raptor Train network architecture and tiering structure.
Cybersecurity researchers have uncovered a new botnet constructed using devices from small office/home office (SOHO) networks and IoT devices. This botnet is believed to be operated by the Chinese hacking group Flax Typhoon, also known as Ethereal Panda or RedJuliett.
Named Raptor Train, the botnet has been active since May 2020 and reached its peak in June 2023, at which point around 60,000 compromised devices were under its control. According to Black Lotus Labs, over this period, more than 200,000 devices, including routers, IP cameras, and network-attached storage systems, were identified as part of the botnet, making Raptor Train one of the largest Chinese IoT-based botnets.
The botnet’s infrastructure follows a three-tiered architecture: the first tier consists of compromised SOHO/IoT devices, the second comprises servers responsible for exploitation and management, and the third is made up of central nodes utilizing a tool called Sparrow. Through this tool, the botnet can orchestrate its nodes, disseminating commands to the first-tier devices.
Among the compromised devices are products from well-known manufacturers such as ASUS, DrayTek, Hikvision, TP-LINK, and Synology. The majority of the compromised devices are located in the United States, Taiwan, Vietnam, and Brazil, with the average lifespan of a device within the botnet being approximately 17 days.
In most cases, the attackers do not use persistence mechanisms that survive device reboots, relying instead on the ease of re-exploitation, given the abundance of vulnerabilities and the vast amount of weakly secured equipment available online.
The propagation of Raptor Train is driven by a malicious code known as Nosedive, a variant of the infamous Mirai botnet. This code enables hackers to execute commands, transfer files, and launch DDoS attacks.
The second-tier servers, which manage the botnet, rotate every 75 days and are located in countries such as the United States, the United Kingdom, and South Korea. Over the past two years, the number of these servers has grown from a few to 60.
Several campaigns have been conducted to enhance the botnet’s capabilities since its inception. For instance, the Canary campaign (May to August 2023) actively exploited vulnerabilities in ActionTec and ASUS devices, using sophisticated infection chains to deploy malicious code.
A hallmark of the most recent malicious operation, known as Oriole, was the widespread popularity of a domain used for botnet control. By June 2024, this domain had entered the trusted rankings of Cisco Umbrella and Cloudflare Radar, allowing it to bypass security systems via whitelists.
Although no direct DDoS attacks involving the botnet have been observed yet, experts believe it could potentially be employed in cyberattacks targeting military and government organizations in the United States and Taiwan.


