The Bling Libra group, known as the creator of the ShinyHunters ransomware, has altered its operational tactics, shifting from selling stolen data to extortion. This change came to light following an incident in which Palo Alto Networks specialists identified the group’s new approach.
In the campaign under review, Bling Libra gained access to the cloud resources of a company on the Amazon Web Services (AWS) platform by exploiting legitimate credentials found in public repositories. Although the rights associated with these accounts were limited, the group managed to infiltrate the system and conduct reconnaissance operations. The attackers used tools such as S3 Browser and WinSCP to access the data.
The significance of these tools for security researchers lies in their ability to generate specific events in AWS logs, enabling the differentiation of malicious activities from automated operations. This discovery aids cybersecurity specialists in more accurately tracking activity within cloud environments.
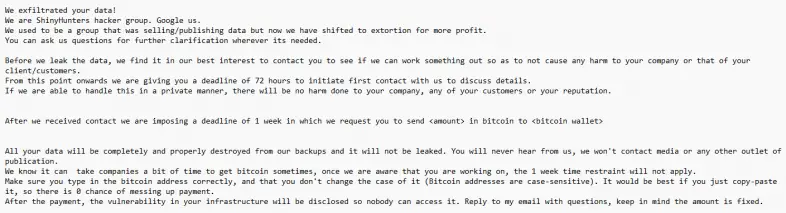
Bling Libra first emerged in 2020 and has since carried out several major attacks, including data breaches of Microsoft GitHub and Tokopedia. The group traditionally exploited legitimate credentials to access databases containing personal information, which they then sold on underground markets. However, in 2024, they shifted their strategy to extorting their victims by demanding ransom in exchange for data preservation.
Upon infiltrating the system, the attackers conduct thorough reconnaissance to assess the resources available to them and later return to execute an attack. In the campaign analyzed by Palo Alto Networks, the hackers deleted some data and created new S3 buckets, likely as a taunt to the organization. After completing the attack, Bling Libra sent the victim a ransom demand.
This incident serves as a reminder of the importance of regular security audits and access rights limitations within cloud systems. Palo Alto Networks recommends using robust analysis and monitoring tools to minimize risks and prevent similar attacks.


