Researchers from the University of Florida and North Carolina State University have identified 119 vulnerabilities affecting LTE and 5G implementations, which could potentially be exploited by attackers to disrupt networks and gain access to the core infrastructure of telecom operators.
The discovered flaws impact seven LTE implementations—Open5GS, Magma, OpenAirInterface, Athonet, SD-Core, NextEPC, and srsRAN—and three 5G implementations—Open5GS, Magma, and OpenAirInterface. They have been assigned 97 unique CVE identifiers.
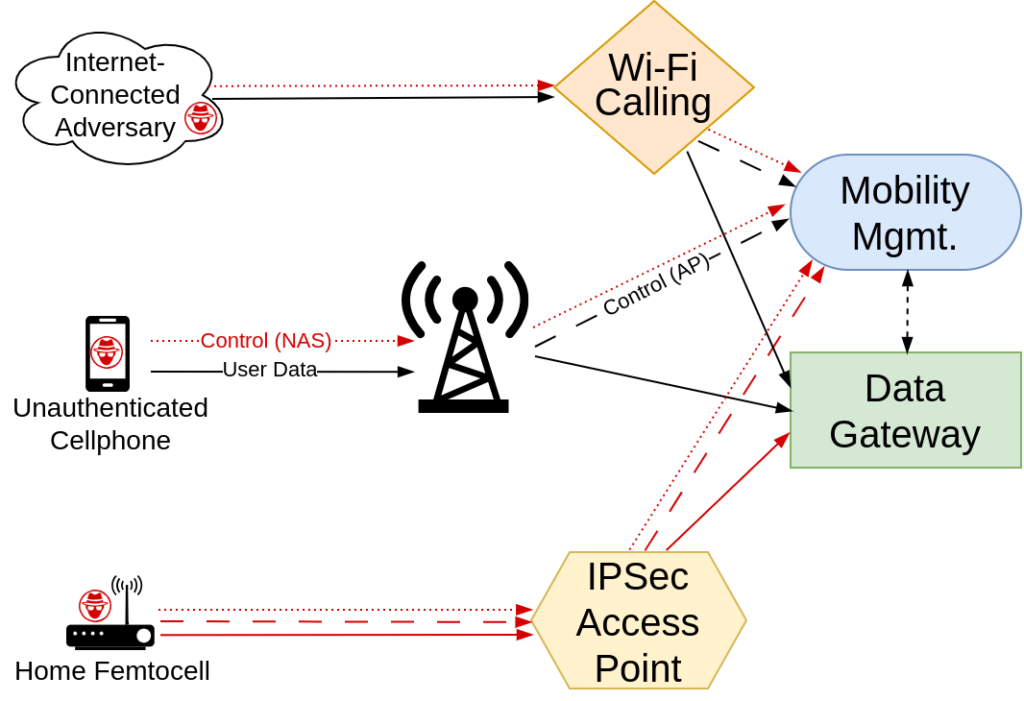
According to the research presented in the report, each of the vulnerabilities could be used to destabilize cellular network operations on a city-wide scale. For instance, an attacker could target critical LTE/5G network functions, such as the Mobility Management Entity (MME) or Access and Mobility Management Function (AMF), by sending a single small data packet without requiring a SIM card.
The foundation of the study lies in a fuzzing methodology called RANsacked, applied to interfaces connecting the radio access network (RAN) with core networks. These interfaces process inputs from both mobile devices and base stations. Many of the vulnerabilities are tied to buffer overflows and memory management errors, potentially enabling attackers to infiltrate the network core, track subscriber locations and connections, and carry out targeted attacks.
The vulnerabilities are divided into two categories: those exploitable by any mobile device without authentication and those accessible after compromising a base station or femtocell. The study revealed that 79 vulnerabilities affect MME implementations, 36 impact AMF, and 4 are related to SGW. Additionally, 25 flaws allow attacks at the Non-Access Stratum (NAS) level before completing the device authentication process.
Particular attention is drawn to risks associated with consumer-grade equipment, such as femtocells, as well as open gNodeB base stations in 5G networks. Once considered secure due to their physical isolation, these devices are now increasingly vulnerable to physical attacks. The report emphasizes that these threats demand a reevaluation of security measures.
The study underscores the urgent need to address the identified vulnerabilities and reassess the security principles of modern mobile networks. The proliferation of new technologies and affordable equipment amplifies the potential risk of attacks, necessitating greater efforts from both developers and network operators.