Before 1994, most scanning technologies relied on one-dimensional barcodes, capable of storing only up to 80 alphanumeric characters. Denso Wave revolutionized this with the invention of QR codes, expanding storage capacity to 7,000 numeric or 4,300 alphanumeric characters.
A study by Cisco Talos revealed that spam filters are largely ineffective against malicious QR codes, as they are unable to detect their presence within images. Statistics show that while QR codes appear in only one out of 500 emails, a staggering 60% of those contain spam or malware.
This emerging form of fraud, known as “quishing,” is still in its infancy. Cybercriminals create counterfeit websites mimicking legitimate platforms and place QR codes in public spaces. For instance, there have been cases of fraudulent QR stickers affixed to parking meters, redirecting victims to fake payment systems.
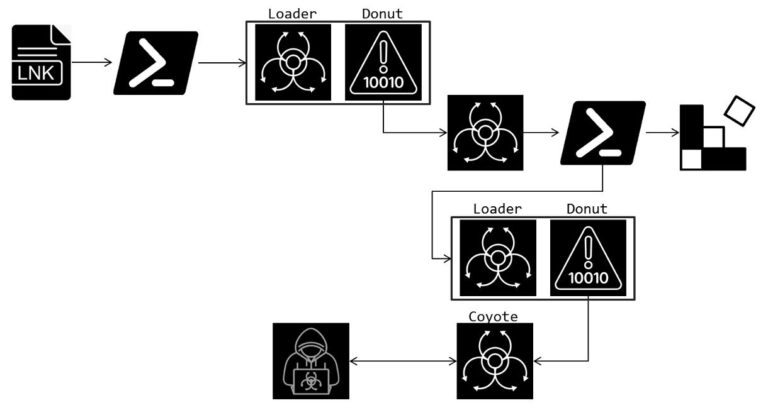
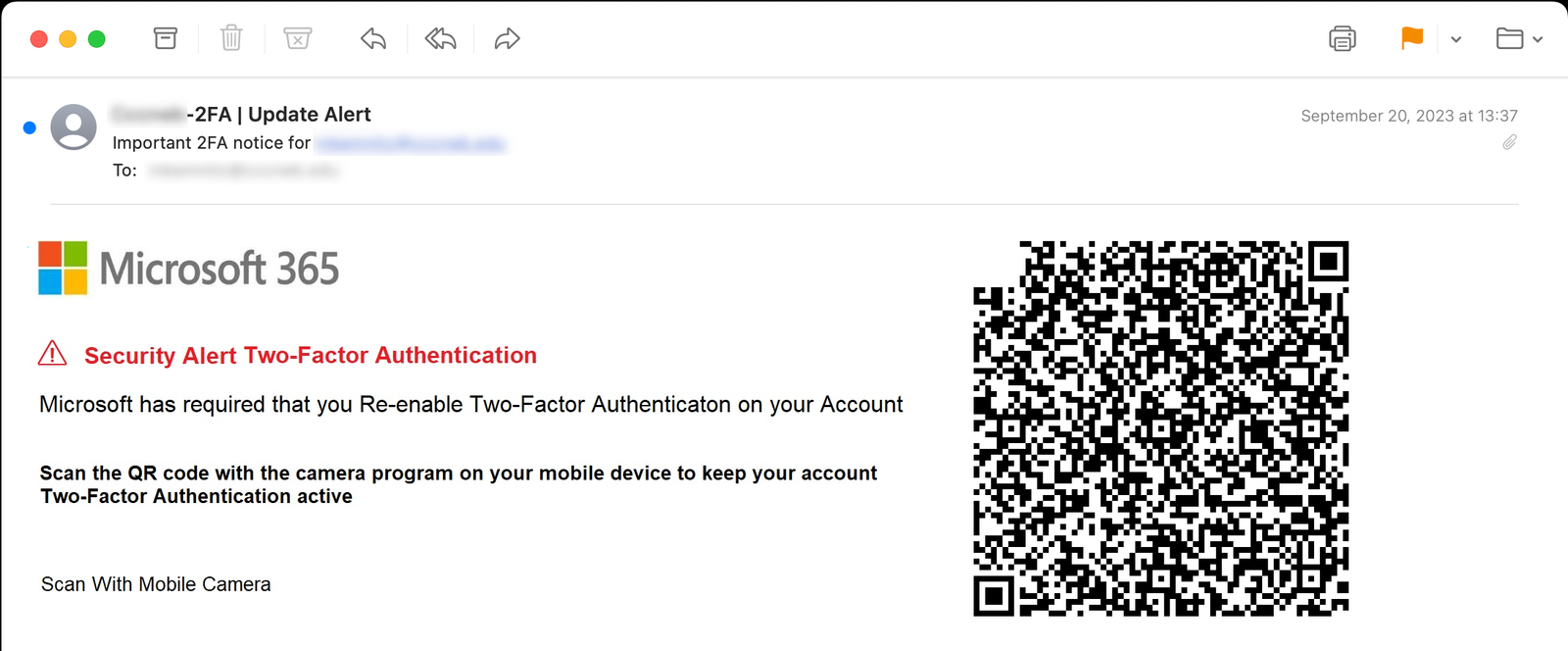
Emails containing QR codes disguised as two-factor authentication requests are among the most common tricks. Scammers use these codes to steal credentials. When scanned, the subsequent traffic between the victim and the attacker bypasses corporate security systems by traveling through mobile networks.
Although such emails account for a small fraction of total email volume (0.1–0.2%), they are significantly more likely to evade spam filters and land directly in inboxes. Moreover, crafty attackers have learned to generate QR codes using Unicode characters, further complicating their detection. Traditional methods for neutralizing malicious links, such as substituting “http” with “hxxp” or inserting brackets into URLs, prove far less effective in these cases.
There are techniques to make QR codes safer, such as masking data modules or removing one or more position detection patterns (the large squares at the corners of the code). However, these methods remain underutilized and poorly understood by the general public.
A distinct threat comes from so-called “QR art”—images where codes are disguised as regular pictures. A user might inadvertently scan such a code with their camera and follow a malicious link without realizing it.
Cisco Talos analysts recommend exercising the same caution when scanning QR codes as when clicking on suspicious links. For frequent users, specialized online decoders can help verify the contents of a code before use.
Remember, while QR technology offers simplicity and convenience, it should never overshadow the importance of adhering to fundamental digital safety practices.