Recently, the Qilin group, notorious for its cyberattacks on the healthcare sector, has once again drawn public attention. Their largest ransom demand to date was $50 million during an attack on Synnovis, a provider of pathology services, significantly impacting several key National Health Service (NHS) hospitals in London.
According to Group-IB, Qilin was first detected in July 2022 and began its operations under the Ransomware-as-a-Service (RaaS) model on underground forums by February 2023. The eponymous Qilin malware, initially developed from the Agenda ransomware in Go, was later reimagined and rewritten in Rust, enhancing its resilience and effectiveness.
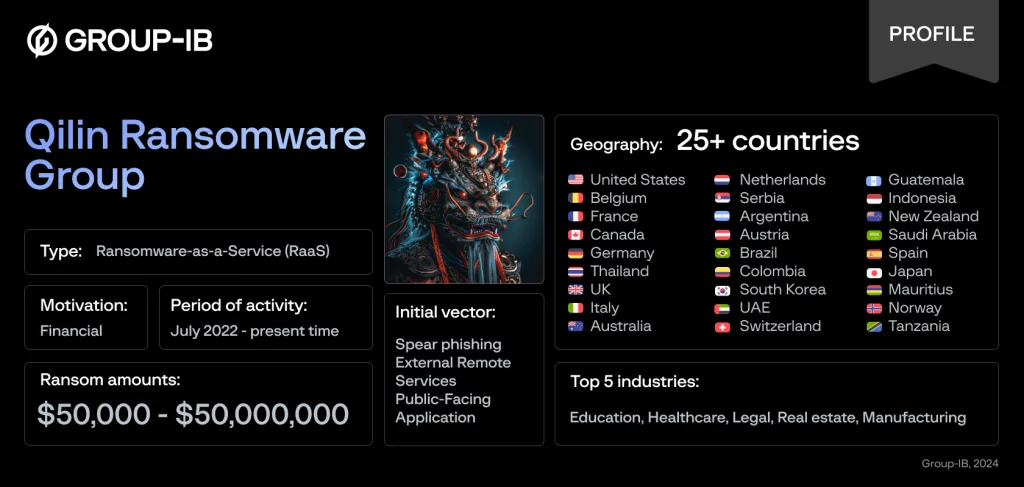
Throughout their activity, Qilin has compromised over 150 organizations across 25 countries, affecting various industries. Research has uncovered a complex organizational structure, including administrative strategies and a network of affiliates.
Qilin’s methods involve exploiting vulnerabilities in well-known devices and software. For instance, the group has leveraged vulnerabilities in Fortinet devices and Veeam Backup & Replication software for initial access. They also employ brute-force attacks on VPN devices and use the Mimikatz utility to elevate privileges on compromised systems.
Qilin actively conceals its activities by deleting system logs and events, complicating incident investigations. The malware can stop processes and services, making detection and response more challenging. A PowerShell command is used for stealthy log removal, clearing Windows event logs.
The Qilin malware is capable of spreading across local networks, functioning as a network worm. It uses the PsExec utility and self-propagation capabilities through VMware vCenter. The malware also employs Remote Desktop Protocol (RDP) and administrative shares for lateral movement within the network.
Additionally, Qilin targets backup systems by deleting data copies and disabling scheduled backup tasks. For data encryption, it uses a combination of AES-256 CTR and ChaCha20 algorithms, rendering data recovery nearly impossible without the decryption key.
Qilin poses a serious cybersecurity threat due to its flexibility and collaboration with various partners within the RaaS framework. The technical tools and methods employed by Qilin continue to evolve, necessitating constant vigilance and updates to protective measures.


