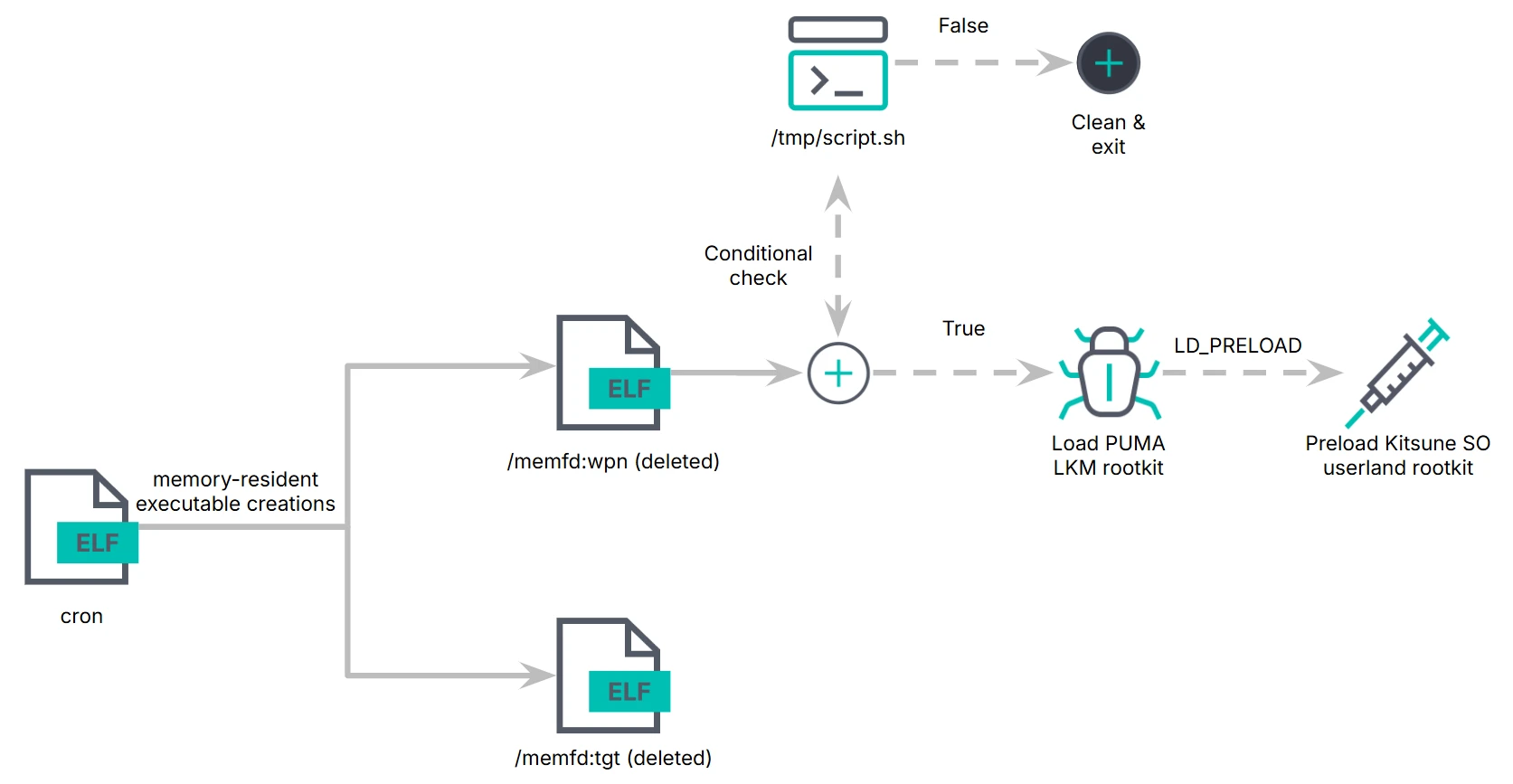
PUMAKIT infection chain
Cybersecurity researchers have uncovered a sophisticated new Linux rootkit named PUMAKIT, designed to conceal its presence, escalate privileges, and evade detection by system tools. This loadable kernel module (LKM) employs advanced stealth mechanisms, making it a formidable threat.
According to Elastic Security Labs, PUMAKIT operates through a multi-layered architecture comprising a dropper component named “cron,” two in-memory executable files (“/memfd:tgt” and “/memfd:wpn”), the LKM rootkit (“puma.ko”), and the Kitsune library (“lib64/libs.so”) for user-space interaction. These components function in tandem to mask the rootkit’s malicious activities.
What sets PUMAKIT apart is its use of Linux’s internal function tracer (ftrace) to hook into 18 system calls and modify critical kernel functions, such as “prepare_creds” and “commit_creds.” This capability enables the rootkit to alter system behavior and facilitate access to concealed functionalities.
The module activates only under specific conditions, such as verifying secure boot settings or the availability of kernel symbol tables. These prerequisites are determined through kernel scanning, with all necessary files embedded in the dropper as ELF-format binaries.
The malware also employs unconventional interaction techniques, including invoking the rmdir() syscall to escalate privileges. These methods add layers of complexity to PUMAKIT’s detection and mitigation.
Every stage of infection is meticulously obfuscated, from using files stored exclusively in ephemeral memory to conducting extensive checks before the rootkit is executed. Analysis has revealed that even seemingly standard components, such as “/memfd:tgt,” are based on a modified Ubuntu Cron binary, while “/memfd:wpn” serves as the rootkit loader.
At present, PUMAKIT has not been linked to any known hacker groups. However, researchers highlight that its intricate architecture reflects the growing sophistication of Linux malware, underscoring the escalating threat these advanced developments pose to systems on the platform.


