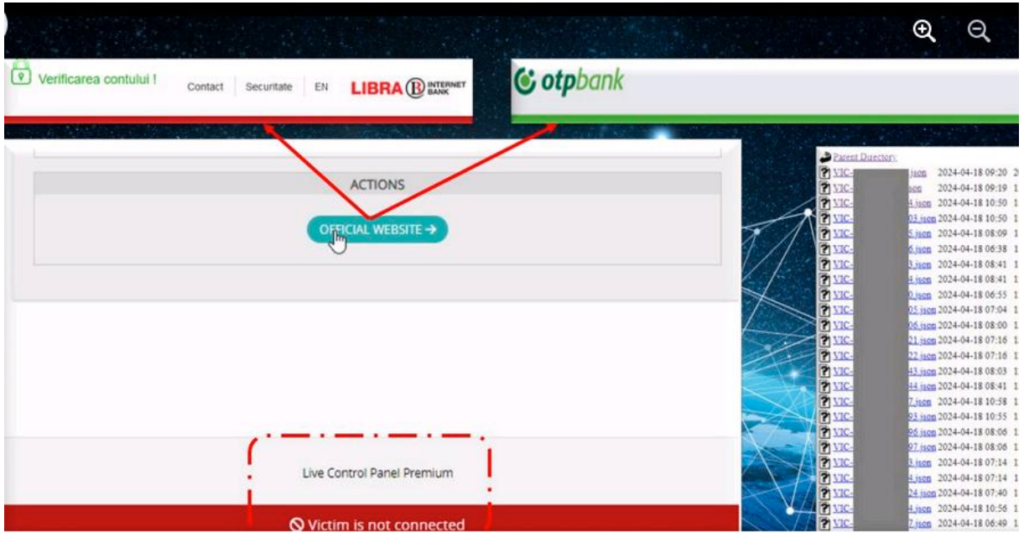
The phishing toolkit “Premium Panel” is being leveraged by cybercriminals in large-scale campaigns across the globe. Research conducted by Intrinsec CTI has revealed that this toolkit operates through a centralized control panel, comprising .php pages and .js scripts designed to harvest victims’ credentials and redirect them to fraudulent login pages.
The primary objective of these attacks is to steal authentication credentials by luring victims onto counterfeit websites that mimic the login portals of well-known companies, predominantly in the banking and logistics sectors. The campaigns have impacted both Western nations and regions such as Saudi Arabia, Israel, South Africa, Taiwan, Qatar, and Guatemala. To evade detection, threat actors host these phishing pages on compromised domains, temporary hosting services, or domains crafted to impersonate legitimate brands.
Intrinsec CTI researchers have devised a tracking methodology to identify newly emerging domains linked to “Premium Panel” by analyzing data from exposed admin panels, including Telegram tokens and unique identifiers. This approach has enabled researchers to map out connections between domains and threats, as well as determine the scope of targeted industries and geographical regions.
Phishing remains a cornerstone of initial access tactics within cybercriminal operations. The accessibility and ease of use of tools like “Premium Panel” empower even less sophisticated actors to orchestrate large-scale campaigns, significantly contributing to the surge in global phishing attacks.
These insights not only allow organizations to respond to incidents more swiftly but also enable them to proactively identify potential threats, thereby fortifying their cybersecurity posture against evolving cyber risks.