On July 16, security researcher Benjamin Mixon-Baca presented a report titled “Attacking Connection Tracking Systems Used by Virtual Private Networks (VPNs)” at the annual Privacy Enhancing Technologies Symposium (PETS). This study uncovered a unique vulnerability in VPN services known as “Port Shadow.”
The research revealed that popular VPN programs such as OpenVPN, WireGuard, and OpenConnect could render users less secure. The vulnerability allows attackers to act as intermediary routers between the user and the VPN server, potentially leading to anonymity exposure, DNS request redirection, or port scanning.
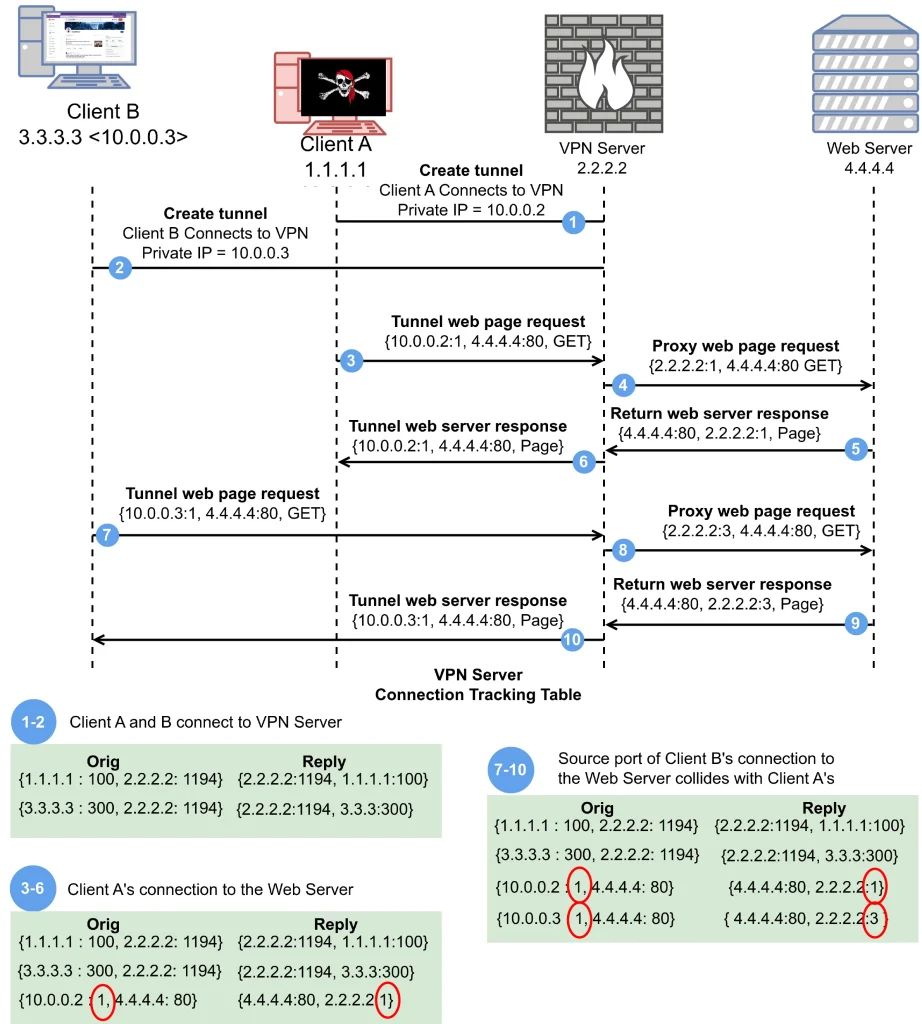
The authors of the study propose several recommendations for VPN providers. These include randomizing the selection of the source port, prohibiting the use of the VPN server’s listening port as the source port, and limiting the number of simultaneous VPN connections. Users are advised to connect to private VPN servers to which they have exclusive access or to use less vulnerable encryption protocols.
The vulnerability was discovered on VPN servers running on Linux and FreeBSD, with Linux servers being the most susceptible to attacks. Developers of VPN programs and operating systems have been notified of the vulnerability; however, due to its specificity, complete mitigation is only possible through certain firewall rules.
The study also highlighted that the vulnerability is particularly dangerous for those using VPNs to circumvent censorship and protect their identity. For instance, journalists or activists could become targets for attackers capable of intercepting and redirecting their traffic.
Users are encouraged to use protocols like ShadowSocks or Tor, which do not rely on vulnerable connection tracking systems. Additionally, it is crucial to utilize VPN servers that host only trusted users.


