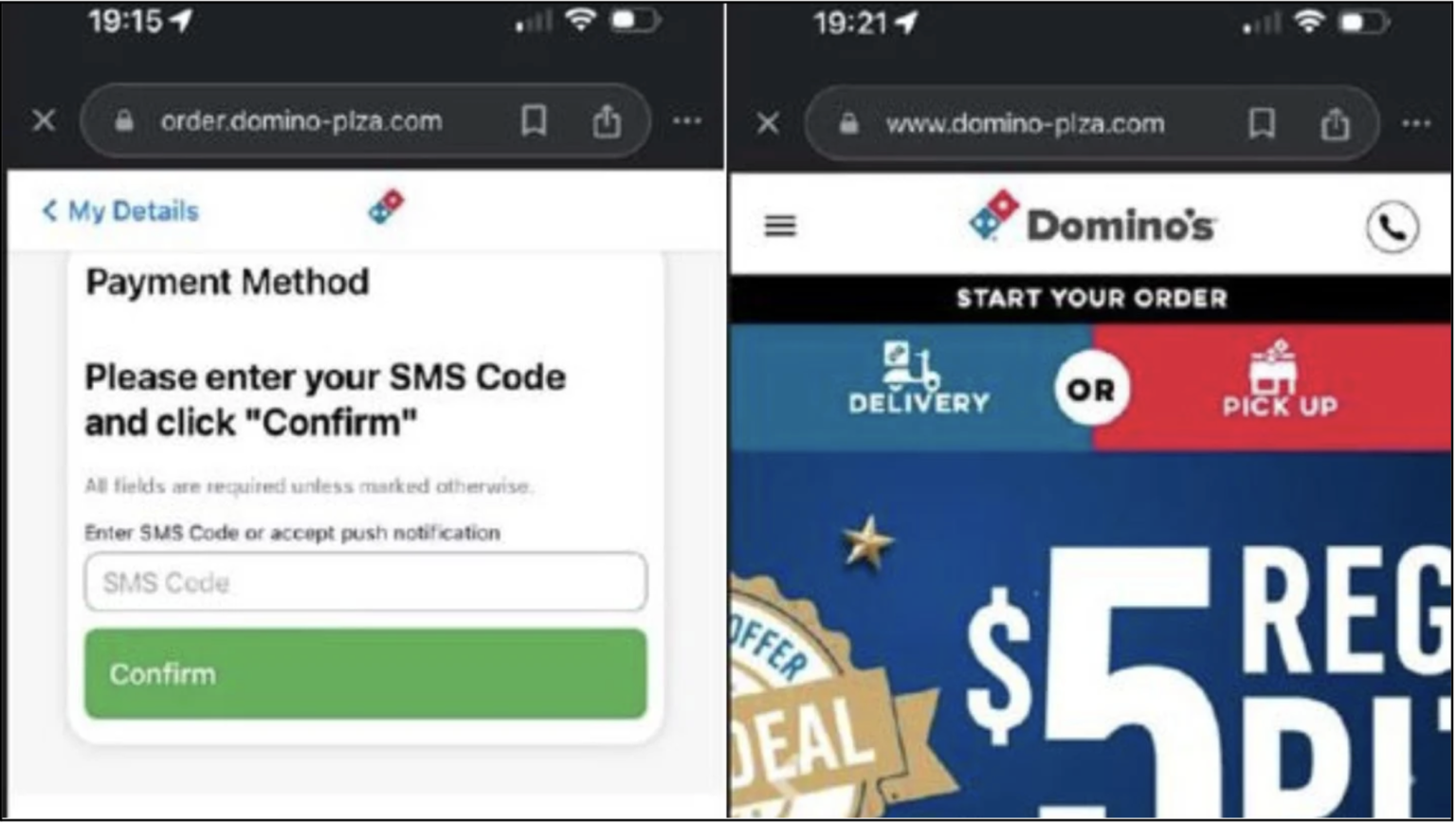
A malicious website replicating the “Dominos” brand for phishing purposes.
Researchers at BforeAI have uncovered a large-scale phishing campaign targeting international pizza chains, resulting in significant financial losses. The investigation began after receiving information from the Singapore Police about a phishing threat, as reported in an article by Yahoo News Singapore. The initial indicator of compromise led to the discovery of a more sophisticated and ongoing attack, spanning multiple countries and targeting various pizza brands.
The campaign was first identified through the domain domino-plza[.]com, which resulted in a loss of 27,000 Singapore dollars from seven victims via fake order pages mimicking the Domino’s Pizza website. The perpetrators used paid search engine ads to elevate their fake domains to the top of search results, surpassing legitimate websites. These tactics, combined with black hat SEO techniques, rendered users vulnerable to phishing.
Following successful attacks in Singapore, the criminals registered domains targeting other major international pizza chains, such as PizzaPizza, Little Caesars, Blaze Pizza, 241 Pizza, Panago Pizza, and Boston Pizza. These domains closely resemble the legitimate ones but contain subtle alterations that can easily mislead users.
The attackers continue to register new domains using IP addresses associated with suspicious domain registrations, often in unusual top-level domains such as “.life” and “.top,” which are atypical for legitimate brands. The attacks begin with the creation of fake websites that are nearly indistinguishable from the originals. When placing an order, users enter a one-time password (OTP), allowing the attackers to capture card details and use them for unauthorized transactions, leading to financial losses for the victims.
The campaign is not confined to a single country and poses a global threat, with a particular focus on Canadian pizza chains. The perpetrators’ ability to register and maintain numerous domains indicates a well-organized operation aimed at exploiting the popularity and trust of these brands.
Although the initial attacks led to substantial losses in 2023, the campaign continues into 2024. There is ongoing activity targeting Canadian pizzerias, including PizzaPizza, Little Caesars, Pizzaiolo, Panago Pizza, and Boston Pizza. The movement of servers and changes in passive DNS records suggest the persistence of this campaign. The use of controversial VPS services, such as Stark Industries, further confirms the involvement of well-equipped cybercriminals.
Recent studies indicate that some phishing domains continue to be updated, signaling the potential for future attacks. The emergence of new domain registrations linked to the same group of attackers underscores the need for constant threat monitoring.
The attacks are also expanding to other organizations beyond the pizza industry, highlighting the importance of increased vigilance and proactive measures to prevent further financial losses.


