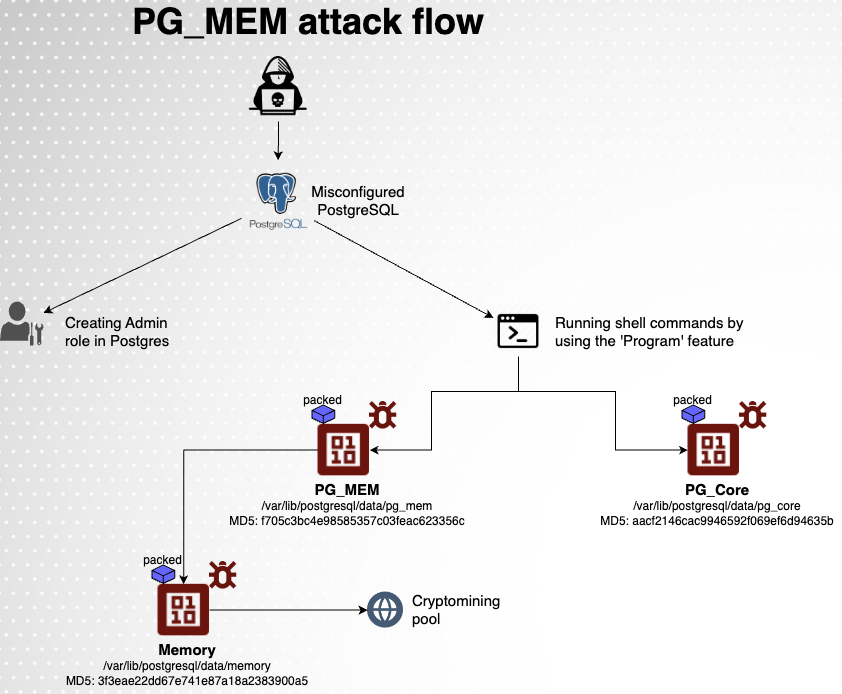
Cybersecurity researchers have uncovered a new malware called PG_MEM, designed to compromise PostgreSQL databases for cryptocurrency mining. This malicious software employs a brute-force technique to crack database credentials and subsequently execute harmful operations.
Assaf Morag, a security expert at AquaSec, explained in his technical report that attacks on PostgreSQL databases commence with repeated attempts to guess credentials using weak passwords. Once the breach is successful, attackers can execute arbitrary shell commands on the server, enabling them to steal data or install malware.
The identified attack chain involves targeting improperly configured PostgreSQL databases to create an administrator account and utilize the PROGRAM function to execute shell commands. Following a successful breach, the attackers conduct initial reconnaissance and execute commands to revoke the superuser privileges of the ‘postgres’ account, thereby restricting access for other potential attackers.
Subsequent actions include downloading two malicious programs, PG_MEM and PG_CORE, from a remote server controlled by the attackers. These programs are designed to terminate competing processes, such as Kinsing, establish persistent access on the server, and ultimately deploy a Monero cryptocurrency miner.
The malware leverages the PostgreSQL COPY command, typically used for copying data between a file and a database table. In this case, the attackers exploit the PROGRAM option, allowing the server to run transmitted commands and log their output into a database table.
Although the primary objective of these attacks is cryptocurrency mining, at this stage, the attackers can also execute any system commands, view data, and control the server. The malicious campaign targets PostgreSQL databases accessible from the internet and protected by weak passwords, which AquaSec attributes to misconfiguration and a lack of proper access controls.
Many organizations connect their databases to the internet, but weak passwords and insufficient identity protection measures leave them vulnerable to such attacks. To safeguard their systems, experts recommend regularly updating databases, using strong passwords, and restricting server access from the internet.


