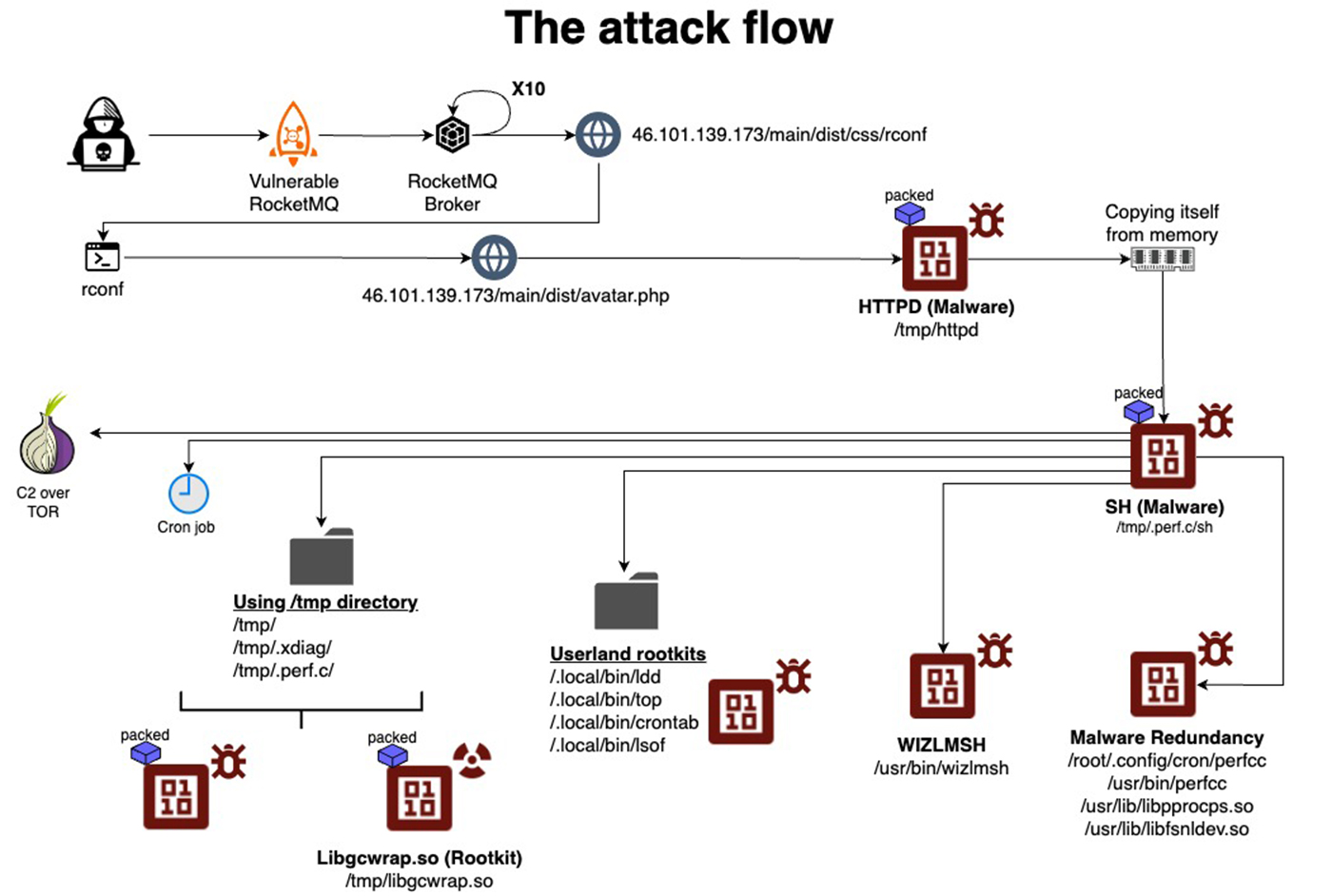
The entire attack flow
Researchers from Aqua Security recently uncovered a campaign targeting vulnerable Linux servers through the deployment of a stealthy malware named perfctl. The primary objective of this program is to exploit compromised server resources for covert cryptocurrency mining and proxy hijacking.
Perfctl is distinguished by its high level of stealth and persistence, achieved through the use of advanced techniques. As noted by researchers Assaf Morag and Idan Revivo, when a new user logs into the server, the malware ceases its “noisy” operations and enters a dormant state until the server becomes idle once more. Upon activation, the malware deletes its binary file and continues to operate in the background as a system service.
Certain aspects of this attack had previously been identified by Cado Security, which discovered a campaign targeting exposed Selenium Grid instances for cryptojacking and proxyjacking.
A unique characteristic of perfctl is its exploitation of a vulnerability in Polkit (CVE-2021-4043, also known as PwnKit), which allows privilege escalation to root and the installation of a miner named perfcc. The name “perfctl” was deliberately chosen to disguise the malware as a legitimate system process, as “perf” is associated with a Linux performance monitoring tool, while “ctl” is a common suffix in various command utilities.
The attack begins by compromising a Linux server via a vulnerable instance of Apache RocketMQ, where a malicious file named “httpd” is uploaded. Once executed, the file copies itself to a new directory, “/tmp,” deletes the original binary, and continues its operation from the new location.
Additionally, perfctl disguises itself as innocuous processes, creates a rootkit to evade security mechanisms, and deploys the miner payload. In some instances, software for proxy hijacking is downloaded and executed from a remote server.
To defend against perfctl, it is recommended to update systems and software regularly, restrict file execution, disable unused services, apply network segmentation, and utilize role-based access control (RBAC) models to limit access to critical files.
The researchers emphasize that perfctl can be detected by unexpected spikes in CPU usage or system slowdowns, which are particularly evident when rootkits are deployed and mining operations intensify during server downtime.


