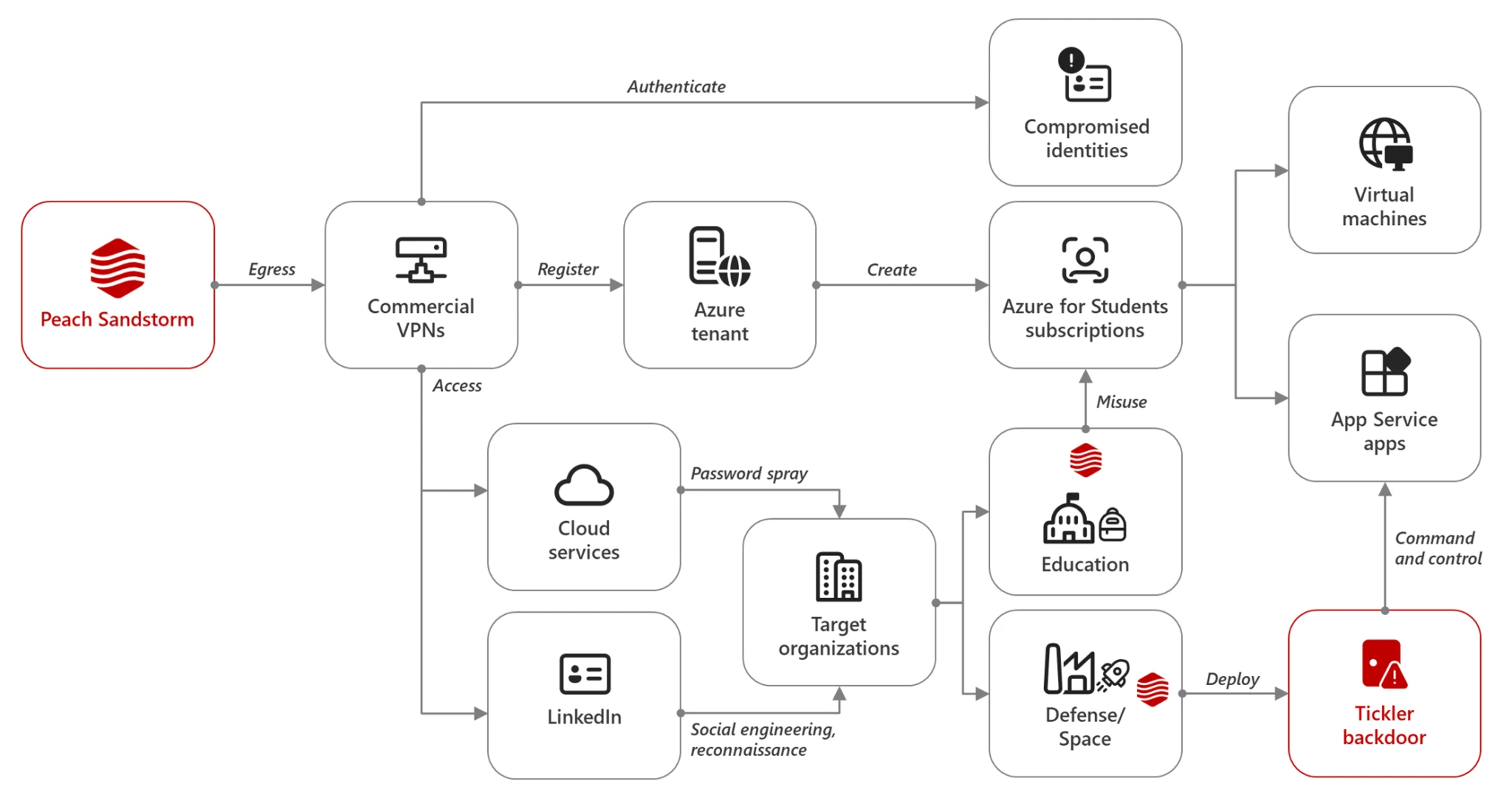
Experts at Microsoft have discovered that the group Peach Sandstorm, linked to Iranian authorities, is deploying a new backdoor named Tickler in attacks targeting satellite communications, the oil and gas sector, and government entities in the United States and the United Arab Emirates.
According to the corporation’s report, hackers from Peach Sandstorm have been using this multi-stage malware since April 2024. The program collects various network information from infected machines and transmits it to the attackers’ command servers.
The first sample of Tickler was found in an archive file named “Network Security.zip” along with two harmless PDF documents. The attack begins by searching the memory for the address of the kernel32.dll library. After decrypting strings, the virus reloads it and launches a legitimate PDF file as bait, titled “YAHSAT NETWORK_INFRASTRUCTURE_SECURITY_GUIDE_20240421.pdf.” Meanwhile, Tickler gathers data on the victim’s network and sends it to the command server via the HTTP protocol.
The second Tickler sample exhibits functionality similar to the first. It downloads additional payloads, including legitimate DLL libraries, from the command server. It also establishes a persistent connection with the server through a resource created in Azure.
Microsoft experts discovered that Peach Sandstorm uses stolen credentials from educational institutions to build their infrastructure in Azure. By doing so, the hackers gain legitimate access to cloud resources and use them to deploy command servers.
In addition to employing Tickler, Peach Sandstorm continues to attack the educational, satellite, defense, and government sectors through password-spraying techniques. Analysts noted that in April and May 2024, the hackers continued to use the “go-http-client” user agent, characteristic of their previous campaigns.
Interestingly, other Iranian groups, such as Smoke Sandstorm, have also been abusing cloud resources in recent months.
Peach Sandstorm is also known for conducting lateral movement within networks after compromising organizations, using the SMB protocol, and attempting to install remote access programs like AnyDesk on infected systems. Additionally, researchers noted that during one intrusion against a satellite operator in the Middle East, Peach Sandstorm utilized the AD Explorer utility to create a snapshot of Active Directory.
To protect systems from Peach Sandstorm’s activities, experts recommend regularly changing passwords for accounts that have been targeted, revoking session cookies, and conducting additional analysis if a compromised account had system-level privileges.
Moreover, it is advisable to implement conditional access policies in Azure to restrict environment access based on specified criteria and to block outdated protocols that do not support multi-factor authentication. For endpoint protection, enabling lockdown mode in Microsoft Defender for Endpoint is recommended so that the program can autonomously block malicious artifacts, even if other antivirus solutions do not detect them.
The identified indicators of compromise, such as malicious files and Azure command servers, can aid in threat hunting within a corporate network. Additionally, Microsoft provides Defender XDR queries to identify related activity and analytical rules in Microsoft Sentinel are available to automatically match IoCs from this report with client data.


