Experts have reported a surge in activity by the Paper Werewolf group (also known as GOFFEE), active since 2022. Over this period, the cybercriminals have executed at least seven attacks targeting organizations in government, energy, finance, media, and other sectors.
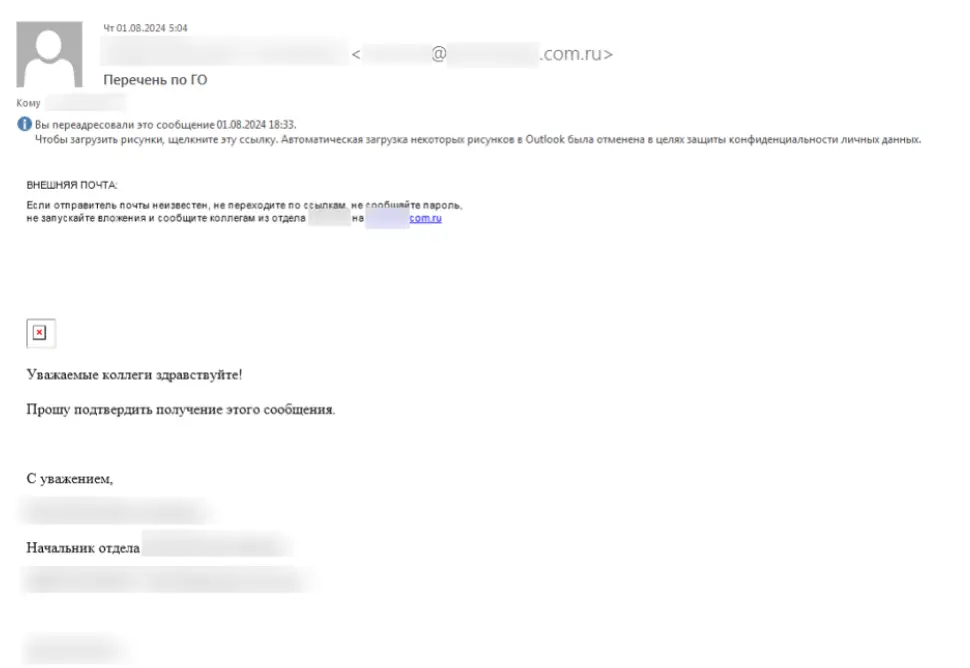
The attackers rely on phishing emails containing Microsoft Word attachments embedded with malicious macros. Once activated by the recipient, these macros decode and execute the malware.
Notably, the group employs the open-source Gophish framework, typically used for testing companies’ susceptibility to phishing, to orchestrate their campaigns.
Phishing emails are often disguised as communications from reputable organizations to build trust with the recipients. However, these entities have no connection to the attacks; their names are misused to camouflage the malicious intent.
Paper Werewolf extensively leverages PowerShell to execute commands, effectively bypassing standard security measures. Their operations are further obfuscated by post-exploitation frameworks and proprietary malware, complicating detection and response efforts.
Among their methods is the deployment of malicious loaders masquerading as legitimate applications. These loaders download additional malware while distracting victims with decoy documents.
In one instance, the group used the IIS module Owowa, which intercepts credentials during authentication on Outlook Web Access. The stolen credentials are stored in volatile memory and can be erased on command.
For maintaining persistence in compromised systems, the attackers utilize hidden scripts and registry modifications. Backup access channels are established using tools like Chisel, allowing them to retain connectivity even when primary methods are blocked.
Paper Werewolf employs a variety of disruptive tactics, including deleting registry entries, rebooting servers, and altering account passwords, significantly hindering recovery efforts and restoring control over the compromised infrastructure.