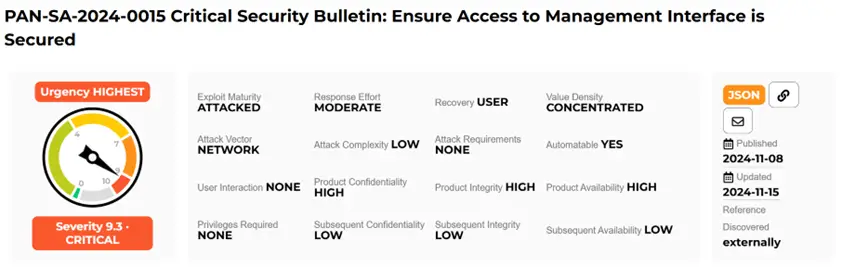
On November 8, Palo Alto Networks urged its clients to promptly enhance the security of firewall management interfaces following rumors of a new vulnerability. Experts from Rapid7 were also monitoring reports of a potential zero-day vulnerability; however, these claims remained unverified until recently.
On November 14, the company updated its advisory, disclosing the confirmed exploitation of an unauthenticated remote code execution vulnerability. Malicious activity has impacted a limited number of firewall management interfaces exposed to the internet.
The company is currently conducting a thorough investigation into the incident. However, as of now, no information regarding a CVE designation or a fix for the identified vulnerability is available.
According to the advisory:
- The risk of compromise is minimal if access to the management interface is restricted.
- No specific indicators of compromise (IoCs) have been identified so far.
- For interfaces accessible from the internet, vigilance is advised for suspicious activities, such as unauthorized configuration changes or the creation of new user accounts.
Notably, Prisma Access and cloud-based NGFWs remain unaffected at this time. Should the situation change, the company has pledged to provide updates.
Until a patch is released, Palo Alto Networks users are advised to ensure that access to the management interface is restricted to trusted internal IP addresses and that the interface is not exposed to the internet. Further guidance is detailed in the Palo Alto Networks advisory.
Additionally, users are encouraged to verify which devices may be accessible from the internet and take appropriate measures if necessary. Experts strongly recommend reviewing the advisory and adhering to all security configurations outlined within.


