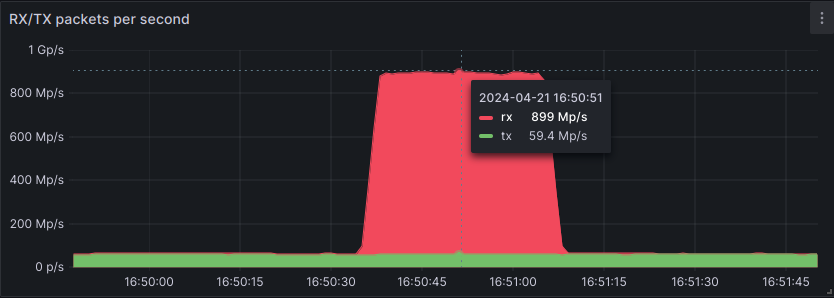
record-breacking DDoS attack mitigated by OVHcloud reaching 840 Mpps
OVHCloud, one of Europe’s leading cloud computing providers, recently disclosed a record-breaking distributed denial-of-service (DDoS) attack, which reached a peak packet rate of 840 million packets per second (Mpps).
Mpps, representing millions of packets per second, is a metric commonly used to describe the performance of network devices such as switches. A packet rate of 840 million per second equates to 840 Mpps.

The attack occurred in April 2024. Following an investigation, OVH identified the likely source of the attack and contacted the relevant manufacturer. However, as of the publication of this report, the manufacturer has not issued any response. The implicated company, MikroTik, is a Latvian manufacturer renowned for producing enterprise-grade routers, switches, and wireless access points.
OVH’s investigation revealed that the source devices of the attack were MikroTik Cloud Core Routers, which by default expose their interfaces to the public internet, making them susceptible to automated scans. The prolonged lack of firmware updates on these devices resulted in security vulnerabilities that attackers exploited to initiate the attack. Specifically, MikroTik’s RouterOS system features a bandwidth test function designed for enterprises to assess network throughput. Attackers could control compromised devices and use this function to generate an enormous volume of packets by issuing concurrent requests.
OVH contacted MikroTik, urging the company to detect and alert customers to upgrade their network device firmware, thereby enhancing security and reducing the likelihood of future attacks. However, MikroTik has not responded to OVH’s request. It remains uncertain whether MikroTik plans to enforce mandatory firmware updates, which is unlikely due to the potential for network disruptions without customer consent.
The DDoS attack utilized 5,000 source IP addresses to conduct a TCP ACK flood. Two-thirds of the packets were routed through four points of presence (PoPs) in the United States, three of which were located on the West Coast.
The identity of the attackers remains unknown, and OVH has not disclosed which industry the targeted customer belongs to. Generally, sectors such as gaming often experience malicious attacks due to competitive pressures, but it is unclear whether the targeted customer in this incident is part of the gaming industry.


