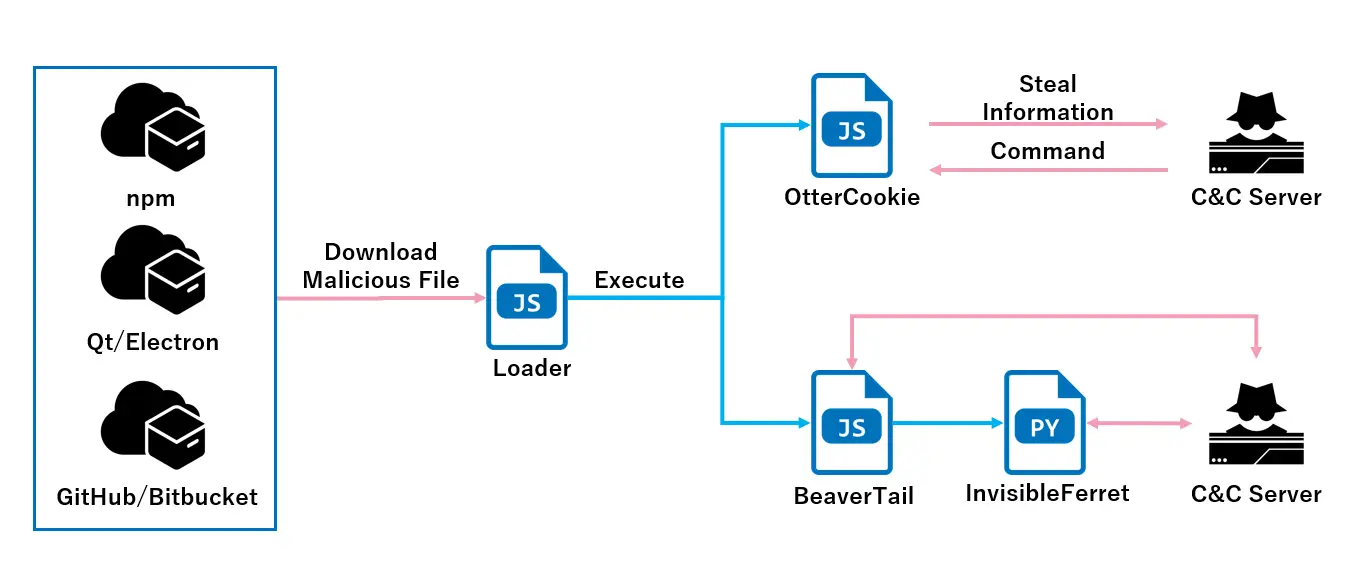
Cybersecurity researchers have uncovered the use of a new strain of malware, OtterCookie, deployed in the Contagious Interview campaign targeting software developers. This campaign, active since December 2022, previously gained notoriety for employing malware such as BeaverTail and InvisibleFerret.
According to a report by NTT Security Japan, OtterCookie first emerged in September this year, with an updated version identified in November. The malware is delivered via a loader that extracts JSON data and executes JavaScript code embedded within the “cookie” property. The primary infection vectors include Node.js projects, npm packages, and files built with frameworks like Qt or Electron, often downloaded from platforms such as GitHub and Bitbucket.
Once activated, OtterCookie establishes a secure connection with its command-and-control server and executes commands. A standout feature of the malware is its capability to steal sensitive information, including cryptocurrency wallet keys, documents, images, and other private data. The September version featured an embedded function for Ethereum key extraction, which was replaced with remote command execution capabilities in the November variant.
Researchers also highlighted OtterCookie’s ability to intercept clipboard data and execute reconnaissance commands such as “ls” and “cat,” indicating preparations for deeper system infiltration. The campaign underscores the attackers’ ongoing experimentation with attack methods and their diverse infection tactics.
Experts advise developers to exercise caution when receiving job offers, thoroughly vet potential employers, and avoid executing unfamiliar code on their devices.


