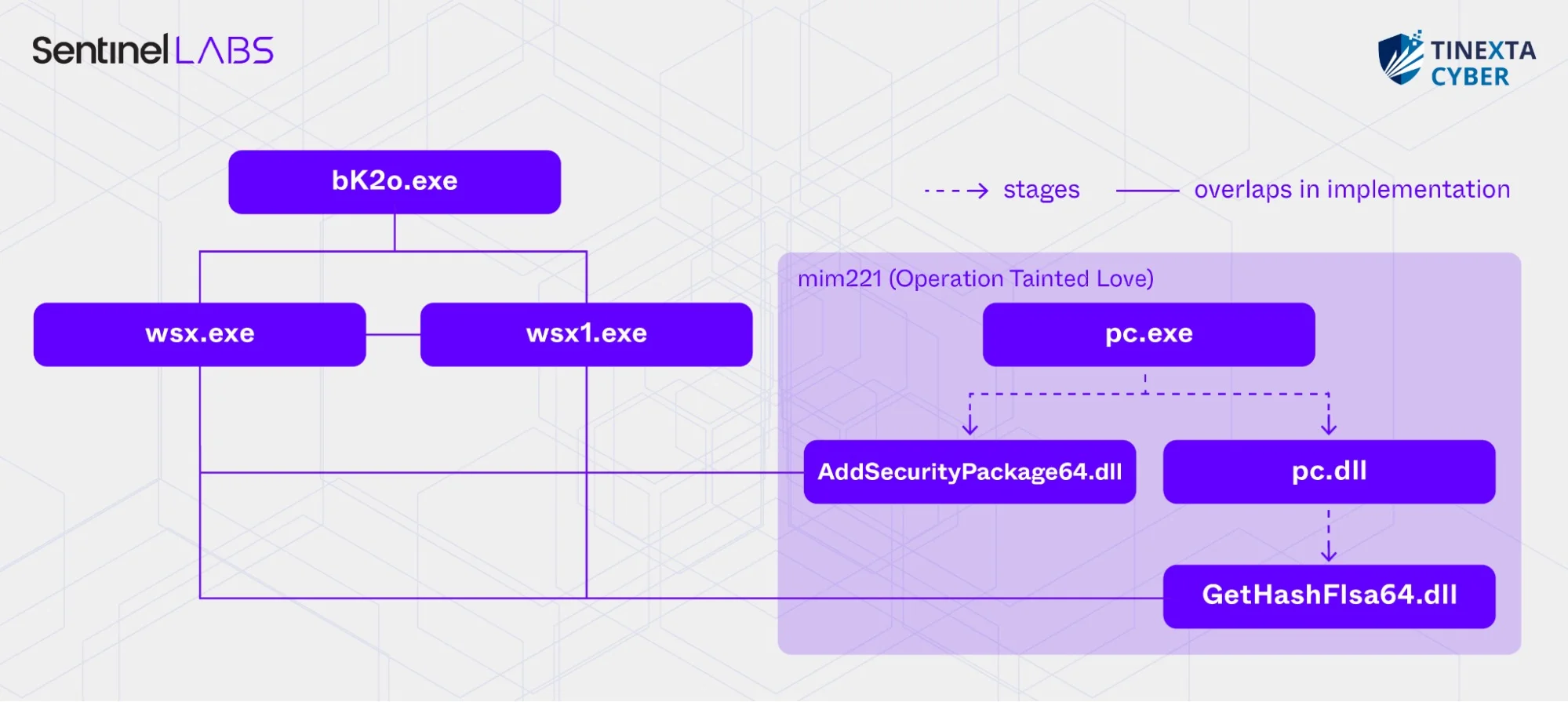
The mimCN samples bK2o.exe, wsx.exe, wsx1.exe, and mim221
A cybercriminal group, allegedly linked to China, orchestrated digital attacks targeting major IT companies in Southern Europe. The campaign, dubbed “Operation Digital Eye,” was detected between late June and mid-July 2024. SentinelOne and Tinexta Cyber reported that the threat was neutralized before any data leakage occurred.
Experts Alexander Milenkoski and Luigi Martire explained that the attackers sought to establish strategic footholds for deeper infiltration into the infrastructures of affected companies’ clients. They leveraged Microsoft Azure and Visual Studio Code to conceal their malicious activities.
The primary attack vector involved exploiting the legitimate Visual Studio Code Remote Tunnels feature. This enabled the attackers to remotely control systems, execute commands, and alter files, effectively disguising their traffic as routine operations and complicating detection efforts.
The initial phase of the attack commenced with SQL injection using the SQLmap tool. Once penetration was achieved, a PHP web shell named PHPsert was deployed to ensure persistent access. Subsequently, the cyberespionage operators conducted reconnaissance, harvested credentials, and traversed the network using RDP and Pass-the-Hash techniques.
For Pass-the-Hash attacks, the perpetrators employed a modified variant of Mimikatz, known as mimCN. This tool has been associated with other Chinese cyberespionage campaigns, including Operation Soft Cell. Overlapping code characteristics and distinctive features confirm its origin from a singular development team.
Throughout the operation, SSH and Visual Studio Code Remote Tunnels were extensively utilized to execute remote commands. The attackers connected using GitHub accounts, though it remains unclear whether these accounts were newly created or compromised.
Further indicators of Chinese involvement include Simplified Chinese comments embedded in the PHPsert code, the use of infrastructure from the Romanian provider M247, and tactics aligning with the Mustang Panda group. Additionally, the attackers’ activities coincided with standard working hours in China.
Operation Digital Eye exemplifies a sophisticated cyberespionage strategy: targeting IT service providers to propagate threats through supply chains. The use of Visual Studio Code Remote Tunnels underscores the pragmatic ingenuity of Chinese APT groups in masking their operations as legitimate activity.


