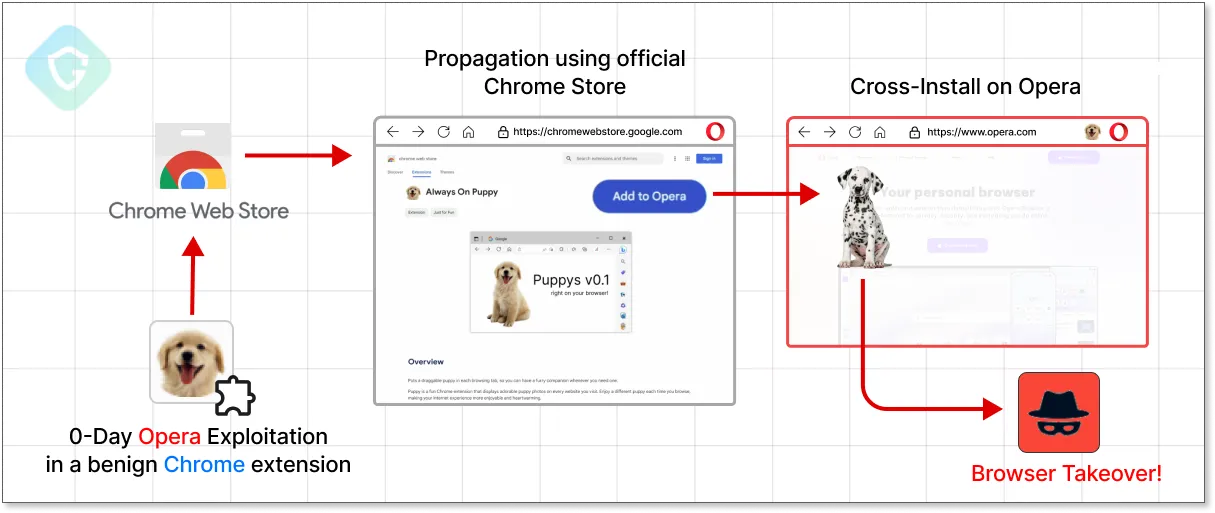
A Puppy-Themed extension on Chrome’s store, crossing the line to Opera and exploiting a 0-Day
A vulnerability was discovered in the Opera browser, allowing malicious extensions to gain unauthorized access to private APIs. According to Guardio Labs, the vulnerability, named CrossBarking, could enable attackers to take screenshots, alter browser settings, and hijack user accounts.
Guardio Labs demonstrated the issue by publishing an ostensibly harmless extension in the Chrome Web Store. When installed in the Opera browser, this extension exploited the vulnerability, transforming the attack into a cross-browser exploit. This case underscores the delicate balance between convenience and security, illustrating how modern threats can exploit covert methods, noted Guardio Labs head Nati Tal.
The vulnerability was patched by Opera on September 24, 2024, after developers were informed of the threat. However, this is not the first instance of vulnerabilities being detected in this browser. Earlier in the year, another issue was identified related to the My Flow feature, which allowed files to be executed on the operating system.
The primary attack method hinges on the fact that certain Opera subdomains have privileged access to closed APIs embedded in the browser. These subdomains, such as Opera Wallet and Pinboard, are also used for internal development purposes. Guardio Labs found that content scripts in browser extensions could inject malicious JavaScript into subdomains with excessive access rights, thereby gaining access to the APIs.
Such access permits attackers to take screenshots, extract session cookies to hijack accounts, and even modify the browser’s DNS settings, redirecting users to controlled DNS servers. This opens the door to “man-in-the-middle” attacks, where victims may be redirected to fraudulent banking and social media sites.
The extension could be uploaded to any extension repository, including the Chrome Web Store, and with JavaScript execution permissions, launch attacks on specific domains with API access. Guardio Labs emphasizes the importance of caution when installing extensions, especially given that official stores are often exploited to distribute malicious software.
Guardio Labs also highlighted that the power of browser extensions can be dangerous, underscoring the need for stricter controls to protect users. They suggest not only enhancing the review process but also requiring real developer identification to prevent account registrations using free email and prepaid cards.


