The OceanLotus group has once again drawn the attention of cybersecurity experts at QiAnXin. After a hiatus at the end of 2023, the group resumed its activities in November 2024 but was swiftly neutralized through the concerted efforts of cybersecurity researchers.
Initially active in 2022, OceanLotus demonstrated a markedly advanced level of attack sophistication compared to its earlier operations, employing zero-day vulnerabilities to steal sensitive data in China’s military, energy, and aerospace sectors.
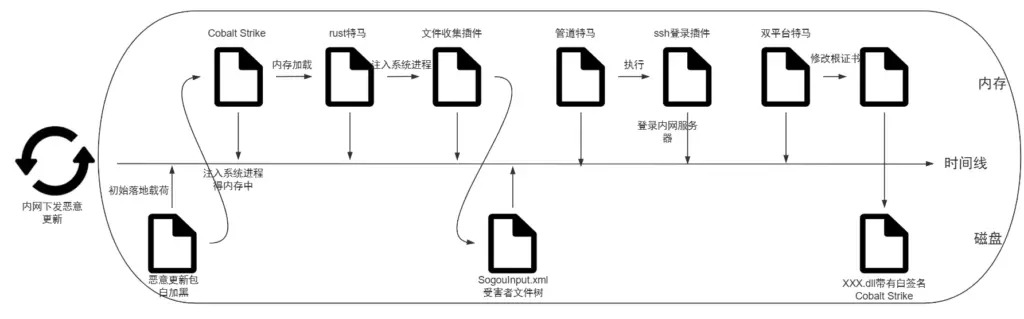
The group specialized in supply chain attacks, embedding malicious updates into target endpoints within corporate networks. Their techniques included leveraging an enhanced version of Cobalt Strike, which captured screenshots from infected devices and transmitted them to a command-and-control server, enabling real-time monitoring of victim activities.
Key tools employed by OceanLotus:
- File collection plugins: These gathered documents with specific extensions, such as PDF, PPT, and XMind files, encrypted them using the AES algorithm, and sent them to the attackers.
- SSH plugins: Utilized to gain access to Linux servers with weak or vulnerable passwords.
- Cross-platform trojans: A specialized malicious code designed to function on both Windows and Linux, enabling server compromise and evasion of security systems.
OceanLotus devised sophisticated methods to bypass antivirus solutions like 360 Security Guard and Skyrocket EDR, employing DLL files and disabling protective processes. Despite the complexity of their tactics, security specialists successfully detected and thwarted their latest campaigns in a timely manner.
Investigations indicate that the group operates out of a Southeast Asian country. Their attacks primarily target the collection of intelligence on Chinese infrastructure and energy projects, aligning with the strategic interests of certain external states that may potentially support the group.
The activities of OceanLotus underscore the critical need for continuous advancements in cybersecurity. Nations and organizations whose data may be of interest to cyber-espionage groups must actively invest in cutting-edge defensive solutions.
Even the most sophisticated attacks can be mitigated when efforts are coordinated, knowledge is shared, and vulnerabilities in supply chains are fortified. Vigilance and adaptability remain the cornerstones of protection in the digital era.