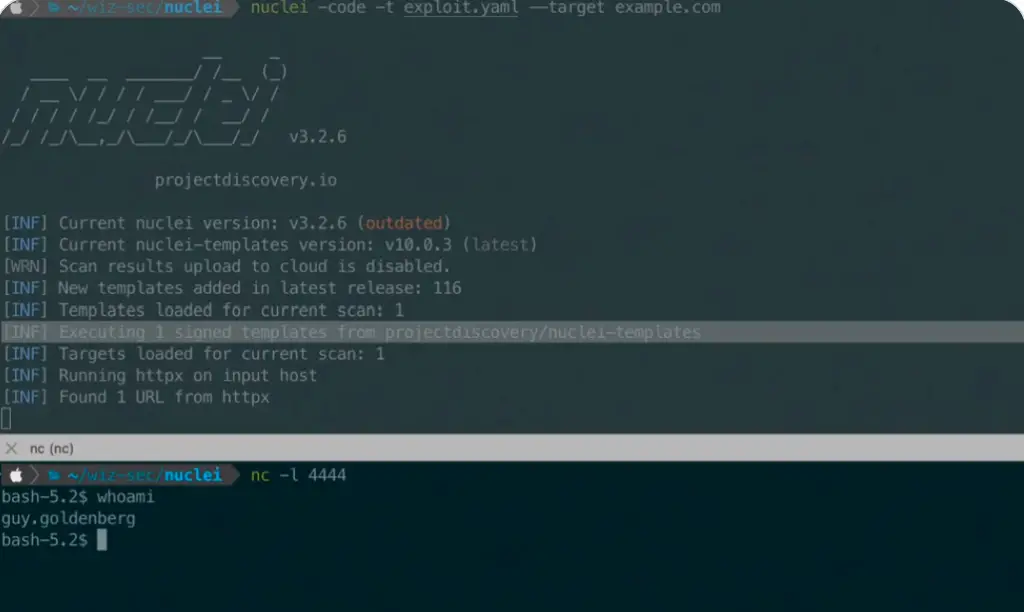
A vulnerability has been identified in the widely-used vulnerability scanning tool Nuclei, developed by ProjectDiscovery. Designated as CVE-2024-43405, this flaw allows attackers to bypass signature verification and execute malicious code. With a CVSS score of 7.4 out of 10, the vulnerability affects all versions of Nuclei starting from 3.0.0.
The issue arises from discrepancies in how newline characters are processed by the signature verification mechanism and the YAML parser. Coupled with the way multiple signatures are handled, attackers can inject malicious code into templates while retaining a valid signature for the benign portion.
Nuclei is widely employed for scanning applications, cloud infrastructure, and networks for vulnerabilities using YAML-based templates. The vulnerability compromises the integrity verification process for templates stored in the official repository, enabling the injection of malicious data while circumventing verification checks.
Researchers at Wiz discovered that attackers could exploit inconsistencies in newline character handling between regular expressions and the YAML parser. Specifically, the \r character can be used to bypass signature checks and enable code execution by the YAML parser.
Exploitation of the vulnerability enables attackers to craft templates with multiple lines bearing the signature marker # digest:. Only the first line is verified, while subsequent lines are ignored during verification but executed by the parser. Furthermore, the improper removal of signature lines during processing allows unauthorized data to be executed.
ProjectDiscovery addressed the vulnerability on September 4, 2024, with the release of version 3.3.2. The latest version, 3.3.7, is available, and users are strongly urged to update to this version.
The researchers noted that the vulnerability is particularly problematic in scenarios where organizations utilize publicly available or unvetted templates without conducting proper security audits. This practice creates a potential attack vector for adversaries. Successful exploitation could lead to arbitrary code execution, data theft, or system compromise.


