Silverfort has identified a vulnerability that allows the circumvention of safeguards against the outdated NTLMv1 protocol, even when Group Policies in Active Directory are enabled. The research revealed that improperly configured local applications can activate NTLMv1, effectively bypassing established security settings.
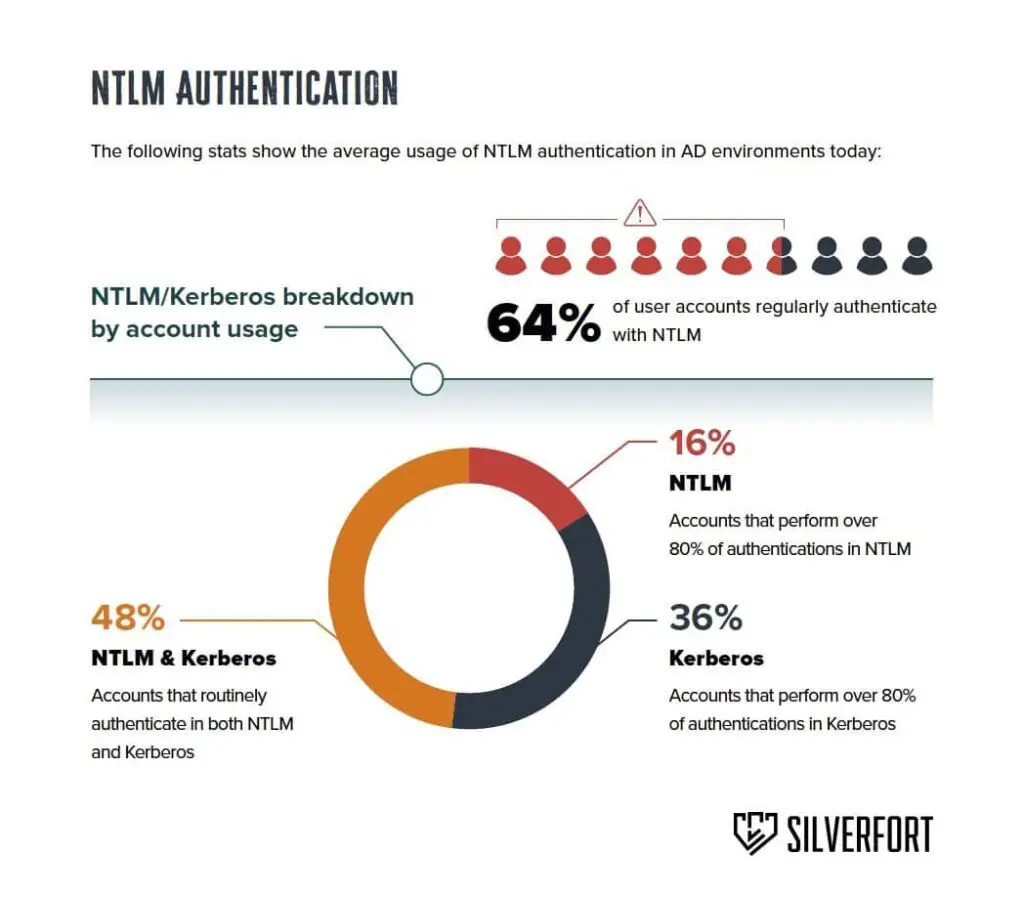
NTLMv1 relies on antiquated cryptographic algorithms and methods, rendering it susceptible to relay attacks and password cracking. Despite Microsoft’s longstanding recommendations to migrate to more secure protocols, 64% of Active Directory accounts continue to regularly utilize NTLM.
This vulnerability is particularly perilous for organizations that rely on legacy or proprietary applications incompatible with modern standards. For instance, macOS devices connecting to banking systems can become easy targets for attackers.
Adversaries who gain access to NTLMv1 traffic can intercept credentials and exploit them for privilege escalation or lateral movement within a network. Silverfort’s experts have demonstrated that this vulnerability is actively exploited in the wild.
In response, Microsoft has announced that NTLMv1 will be entirely removed from Windows 11 (version 24H2) and Windows Server 2025, marking a significant milestone in enhancing security by phasing out obsolete protocols.
The study further highlighted that even with active protections in place, the vulnerability persists due to local application settings. Organizations are advised to maintain logs of NTLM authentications, identify vulnerable applications, and transition to modern security measures such as Kerberos.
Silverfort advocates for a risk-based approach to security, emphasizing the modernization of authentication methods. The company’s report validates Microsoft’s decision to eliminate NTLMv1, underscoring the importance of adopting contemporary, secure solutions to safeguard IT infrastructure.