According to a new report from Secureworks, North Korean government operatives, covertly hired as IT workers in the U.S., U.K., and Australia, have begun extorting companies after gaining access to their internal data.
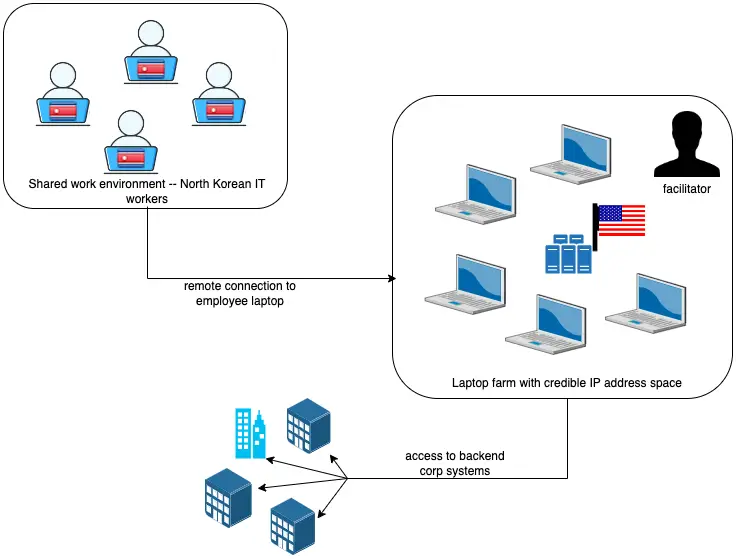
The specialists identified several technical and behavioral indicators typical of such schemes. In some cases, the fraudsters, once employed under false documentation and having gained access to internal systems began extorting money from their employers. One such incident occurred in mid-2024 when a new employee stole confidential data immediately after starting the job. These attacks bear resemblance to the tactics used by the NICKEL TAPESTRY group, which previously employed IT scammers to fund North Korea’s military program.
After being hired under falsified documents, the fraudsters demanded ransom from their former employers, leveraging the stolen data. In one instance, the new employee managed to copy confidential information soon after starting work in mid-2024. The scammer transferred corporate data to their Google Drive using VDI. To obfuscate their activity, they utilized IP addresses from the Astrill VPN network and proxy servers.
After being dismissed for poor performance, the company received a series of emails demanding cryptocurrency payments to prevent the publication of the stolen documents. The emails included archives proving the data theft. In another message, sent from a different email service, the scammer provided additional evidence of the theft, further emphasizing the seriousness of their intentions.
Secureworks notes that the incident highlights the expansion of North Korea’s operation: beyond extortion and data leaks, they are now targeting intellectual property for financial gain.
One common tactic involves altering the delivery address for corporate laptops to decoy locations, known as laptop farms. In some cases, the fraudsters preferred to use personal devices instead of company-issued equipment or connected via virtual desktops (VDI), which allowed them to mask their location and complicate incident investigations.
The perpetrators also used AnyDesk and Chrome Remote Desktop for unauthorized remote access, activities unrelated to their official duties. An analysis of the connections revealed that these programs were configured to operate through Astrill VPN, indicating a connection to NICKEL TAPESTRY’s toolkit.
North Korean specialists have also been known to avoid video calls, though recently they have started using software like SplitCam, which helps conceal their identity during video conferences by allowing them to participate in multiple calls with a single webcam. Secureworks suggests that the use of such tools reflects an effort to adapt to companies’ growing demands for video communication.
The financial behavior of the scammers also raised suspicions. They frequently changed bank accounts for receiving their salary, using digital payment services such as Payoneer to circumvent traditional banking systems. These financial manipulations are a hallmark of NICKEL TAPESTRY’s schemes.
Investigations revealed that the scammers sometimes infiltrated the same company in groups. They would recommend each other for positions and operate under different identities. In some cases, one person would use multiple accounts, adjusting their writing style to different roles, creating the appearance of several employees.
The shift to ransom extortion marks a new phase in NICKEL TAPESTRY’s tactics. These actions increase the risk for companies, as the fraudsters not only collect salaries but also threaten to release stolen data. Organizations hiring remote IT specialists should be particularly vigilant when candidates exhibit the following characteristics:
- Applying for full-stack developer roles;
- Claiming 8-10 years of experience and listing 3-4 previous employers;
- Displaying beginner to intermediate English language proficiency;
- Submitting resumes with elements recurring in other candidates’ applications;
- Refusing to turn on their camera during interviews or using virtual backgrounds;
- Sounding as though they are speaking from a call center;
- Changing delivery addresses and banking details during the hiring process.
Secureworks recommends verifying candidates’ documents for authenticity and conducting video interviews to detect suspicious behavior. Additionally, companies should limit the use of unauthorized remote tools and monitor changes in payroll methods.


