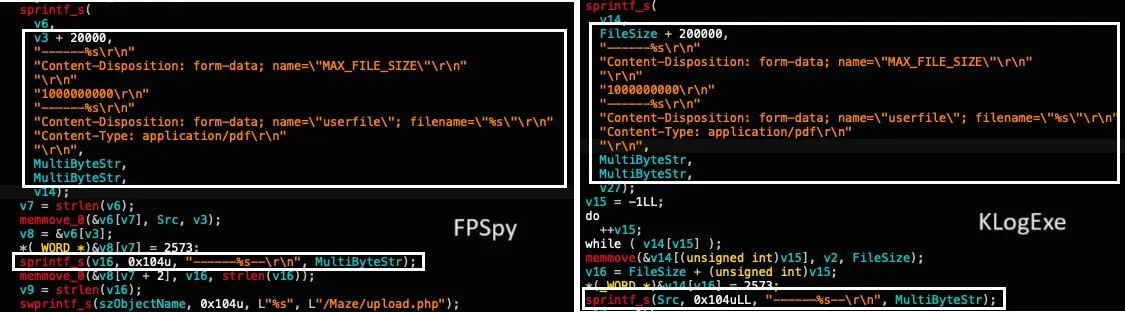
Comparison between FPSpy and KLogExe’s HTTP packet structure
Researchers at Palo Alto Networks have detected new activity from the North Korean hacker group Kimsuky, which employed two new malware strains in their attacks — KLogEXE and FPSpy. Experts claim that these tools expand the group’s arsenal, showcasing its evolution and growing capabilities.
Kimsuky, also known as APT43, ARCHIPELAGO, Black Banshee, Emerald Sleet, Sparkling Pisces, Springtail, and Velvet Chollima, has been active since 2012, specializing in spear-phishing attacks — sending malicious emails disguised as messages from trusted sources.
According to Daniel Frank, Director of Threat Research at Palo Alto Networks, the new malware primarily spreads through phishing attacks. Hackers craft carefully worded emails with content designed to lure victims into opening a ZIP file, which conceals the malicious files. Once these are executed, an infection chain is triggered, ultimately leading to the deployment of KLogEXE and FPSpy.
KLogEXE is a variant of the InfoKey keylogger, written in C++, which was previously uncovered in Kimsuky’s campaign targeting Japanese organizations. FPSpy is a variant of a backdoor first identified by ASEC in 2022, bearing similarities to KGH_SPY malware described by Cyberseason in 2020.
Both malware strains are equipped with functions to gather data on running applications, intercept keystrokes and mouse clicks, and collect system information from the infected device. FPSpy is also capable of downloading and executing additional payloads, running arbitrary commands, and scanning disks, folders, and files on the compromised system.
Unit 42 researchers found similarities in the source code of KLogEXE and FPSpy, suggesting a common development origin. The current Kimsuky campaign is mainly targeting organizations in Japan and South Korea, and according to Dahan, this activity is highly targeted, affecting only specific countries and sectors.
The continuous improvement of hacker groups underscores the need for constant learning and adaptation of defensive measures. Just as in nature, where predators and prey evolve together, the digital realm is marked by an ongoing race between attackers and defenders. Only by understanding this dynamic and investing in the development of skills and defense technologies can organizations ensure their security.


