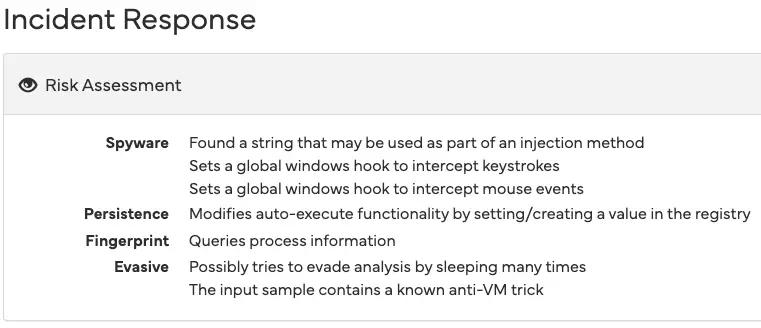
Keylogger sets global hooks to intercept keystrokes and mouse events
A new keylogger associated with the North Korean group Andariel was recently uncovered through analysis on the Hybrid Analysis platform. Also known as APT45, Silent Chollima, or Onyx Sleet, Andariel is believed to target American organizations. Researchers examined the capabilities of this malware, including its functions for recording keystrokes and mouse movements.
One distinguishing feature of the keylogger is its use of “junk” code, which complicates analysis. This code is deliberately embedded to hinder analysts and delay detection. Analysis revealed that the keylogger installs global hooks at the Windows level to capture keyboard and mouse events.
During its operation, the keylogger logs information on pressed keys and mouse actions, which is stored in a password-protected archive. The file is created in a temporary folder, with access to these data secured by a password. Experts found that the keylogger can also modify Windows registry entries, allowing it to remain active even after system reboots.
Additionally, it was found that the keylogger intercepts and records clipboard contents using appropriate system calls. This enables attackers to capture data the user copies, such as passwords or other sensitive information.
The program also timestamps events, recording the date and time of each new action. This approach allows for a more comprehensive view of the user’s activities on the computer.
Andariel’s malware continues to evolve, demonstrating how serious threats adapt to defensive methods and analysis. The inclusion of junk code and evasion techniques complicates the work of security professionals, highlighting the need for constant advancement in cybersecurity tools.
This keylogger is not merely a data collection tool but an example of sophisticated concealment, complicating countermeasures and underscoring the importance of timely detection of such threats.


