Researchers from the DoubleAgent platform have recently observed the activity of a new version of the FASTCash malware, which targets Linux operating systems and is linked to North Korean hacking groups.
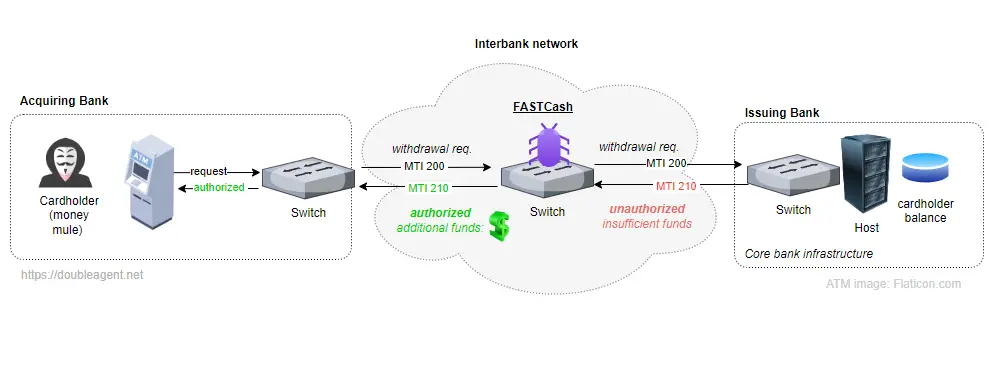
This malware is designed to infiltrate financial networks to facilitate illegal cash withdrawals from ATMs. FASTCash intercepts and alters transaction data processed on payment gateways, enabling the approval of fraudulent withdrawal requests.
Previously, known versions of FASTCash primarily targeted systems based on IBM AIX and Windows. However, the newly identified Linux variant, as the researchers discovered, is tailored for Ubuntu 20.04. The malicious software intercepts messages about declined transactions and approves them, adding random amounts in Turkish lira to the cards.
The research revealed that the Linux variant operates similarly to its Windows counterpart but with certain distinctions. Its main function is to manipulate ISO8583 messages, which are used to process transactions. Like the Windows version, it works with Turkish currency and utilizes unique fields to falsify transaction data.
Notably, the malware exploits vulnerabilities in payment gateways where message integrity checks are absent. This allows FASTCash to alter transactions without detection, generating false approvals for requests indicating insufficient funds by substituting arbitrary amounts.
Researchers also identified signs in the Linux version’s code suggesting the use of VMware virtual machines during development. The malware can be injected into a running process via the ptrace system call, making it difficult to detect without proper security configurations on Linux servers.
Although the Linux variant has more limited capabilities compared to the Windows version, it still poses a significant threat to financial institutions. Its primary objective is to falsify transaction data on devices such as ATMs and POS terminals, enabling attackers to illicitly obtain large sums of money.
To prevent such attacks, experts recommend strengthening the authentication of transaction messages and employing more secure methods such as chip-and-PIN for debit cards, as well as cryptographic verification of transaction responses.


