Infection lifecycle diagram
In June 2024, experts from Mandiant Managed Defense uncovered a cyber-espionage group, UNC2970, which has been linked to North Korea. Later that same month, Mandiant specialists observed phishing attacks in which hackers impersonated an energy company and an organization within the aerospace sector.
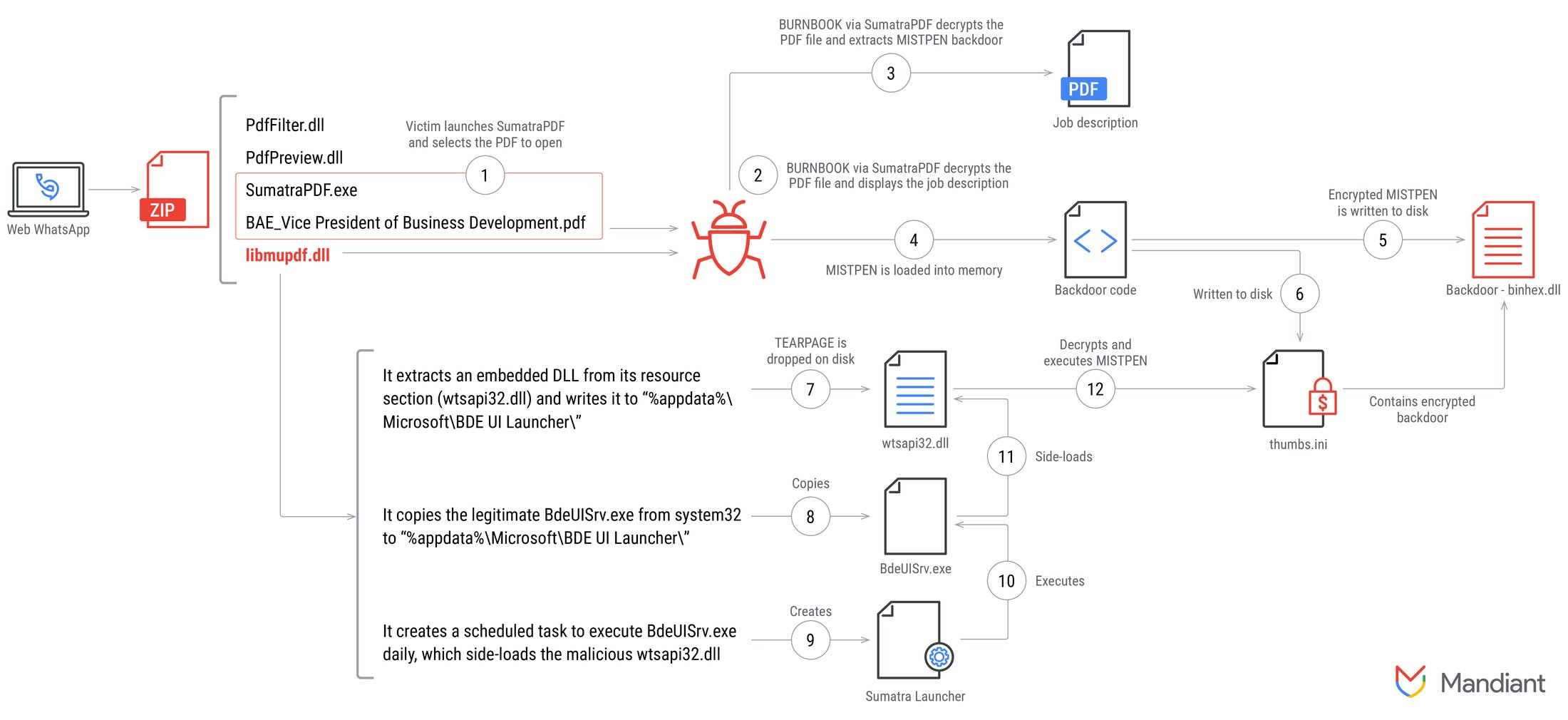
UNC2970 employs fake job offers, posing as recruiters from well-known companies. For each target, the attackers tailor the job description to match the victim’s profile. Contact is initiated via email or WhatsApp, after which the cybercriminals send an archive, purportedly containing a job description in PDF format. However, to open the PDF, the victim is required to use a fraudulent version of SumatraPDF, which installs malware—the MISTPEN backdoor—granting control over the victim’s system.
Mandiant’s investigation revealed that UNC2970 had modified the code of an old version of SumatraPDF. The original SumatraPDF software, however, was not compromised. As a result of the investigation, Mandiant informed the program’s developers of the campaign to raise awareness.
The MISTPEN malware is a modified plugin (binhex.dll) for the Notepad++ text editor, complicating the analysis process. According to researchers, additional features were gradually added to the new version of the backdoor, including network connectivity checks, which further hinder cybersecurity experts’ efforts.
UNC2970 targets individuals connected to critical U.S. infrastructure, with a primary focus on managers and executives who have access to confidential information. The criminals alter original job descriptions by making subtle changes to the qualifications and experience requirements, tailoring them to their chosen victim.
Mandiant experts note that UNC2970’s attacks aim to gain access to strategic information, and their activities overlap with another North Korean group, TEMP.Hermit, which has been active since 2013.
Earlier in 2023, Mandiant specialists reported that North Korean hackers were targeting cybersecurity researchers and media organizations in the U.S. and Europe through fake job offers, leading to the deployment of three new malware families.


