Loaded as Service DLL-SideLoading
Cybereason has published a continuation of its research on the activities of the APT10 hacker group as part of the malicious operation Cuckoo Spear. This new installment examines the malware families NOOPDOOR and NOOPLDR in detail. The objective of the research is to assist cybersecurity specialists in better understanding the adversaries’ methods and tools to enhance network defense.
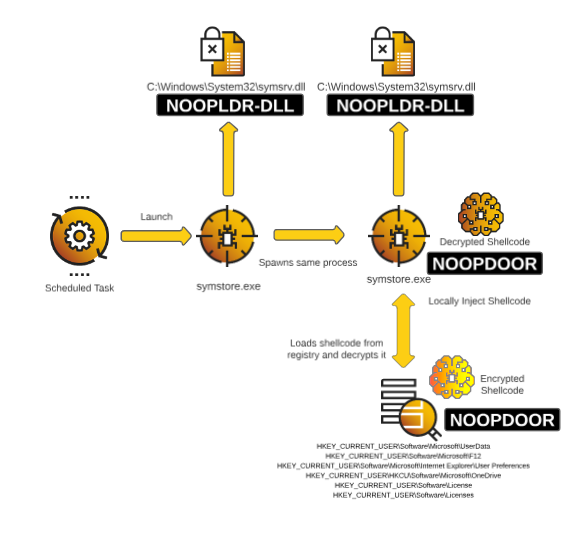
Particular attention is given to the analysis of the NOOPLDR-DLL tool. This malicious code loader can establish persistence in the system by functioning as a service, obfuscating its code to complicate analysis, and concealing strings through XOR encryption. The tool also performs shell injection into processes via modified DLL libraries.
NOOPDOOR is an encrypted shellcode extracted from the Windows registry and decrypted using AES-CBC with MachineId. The malicious code is then injected into process memory. The attackers employ their own system calls to bypass defenses and conceal their presence.
Cybereason also presented an analysis of another version of the loader—NOOPLDR in C#. This version stores malicious code in an XML file and executes it via “msbuild.exe.” Despite heavy code obfuscation, researchers were able to dissect its functionality. It dynamically loads shellcode from a file or the registry, verifies its integrity, and decrypts it.
Additionally, the research delves into the client-side component of NOOPDOOR, which features functionality for interacting with C2 servers. Domain names are generated using a DGA algorithm, allowing the attackers to rotate command server addresses, complicating detection and blocking.
Cybereason also identified a separate server-side component of NOOPDOOR, which is capable of modifying firewall rules, using custom protocols for communication, and executing commands aimed at data theft and controlling the compromised network.
Experts emphasize that APT10’s operations are linked to long-term infiltration of organizational networks. To effectively eliminate the threat, it is recommended to consult an incident response team to carry out a comprehensive network cleanup and prevent the attackers’ return.
For identifying signs of attack and malware exploitation, the research provides search queries that help trace suspicious process behavior and network activity related to Cuckoo Spear.


