The National Institute of Standards and Technology (NIST) has announced that it has successfully processed the backlog of unreviewed vulnerabilities but acknowledged that eliminating the delay entirely by the end of the year remains unattainable.
At the start of the year, it was revealed that due to resource constraints, NIST had left thousands of critical vulnerabilities unanalyzed and without enriched metadata. Enrichment is the process of adding detailed information about vulnerabilities to the NVD database.
With support from CISA and several private organizations, NIST now boasts a fully staffed team of analysts who have begun promptly processing new vulnerability records as they are received. Additionally, all vulnerabilities from the KEV catalog that had been queued for review have now been analyzed. New vulnerabilities are also being processed without delay.
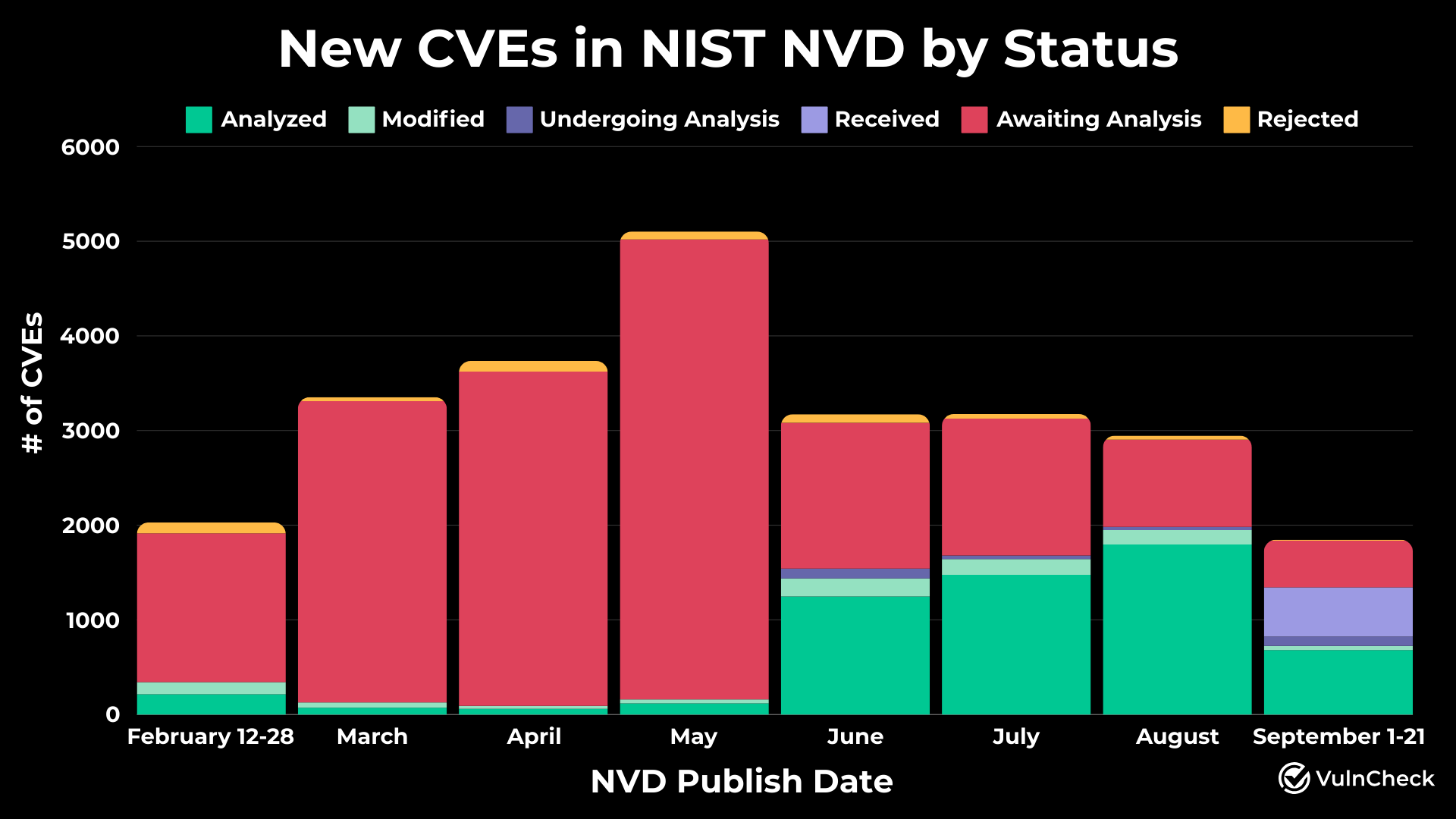
In September, researchers from VulnCheck reported that as of September 21, over 18,000 vulnerabilities—approximately 72.4% of all CVE entries—remained unprocessed in the database. Alarmingly, nearly half of these vulnerabilities had already been exploited by hackers but were yet to undergo detailed analysis.
NIST admitted that its initial plan to address all vulnerabilities by the end of the year was overly optimistic. One significant challenge lies in the data formats provided by authorized data providers (ADPs), such as CISA, which often require additional processing. To address this, new systems are being developed to expedite data handling.
CISA became NIST’s first official data provider this year, enabling the agency to directly integrate new vulnerability data into its system. NIST has not disclosed whether additional providers beyond CISA are involved at this time.
Meanwhile, as of November 18, 2024, the NVD is introducing system updates to enable the collection of more granular data from certified sources such as CNAs and ADPs. CVE entries will now include enhanced information, such as references, CWE classifications, and CVSS scores, which will be displayed on the website and accessible via API. These updates are expected to result in more frequent record updates, urging companies to prepare for an increased volume of data.
Furthermore, the NVD will improve the handling of duplicate references by applying tags automatically to all duplicate links. Updates will also refine the chronology of CVE change history events. Obsolete API parameters, such as HasCertAlerts and HasOval, will be phased out to simplify vulnerability searches. Support for the latest version, CVSS v4.0, will allow for more precise risk assessments based on updated criteria.
Earlier in April, cybersecurity experts sent a letter to Congress and U.S. Commerce Secretary Gina Raimondo, urging additional funding to support the NVD. The letter highlighted the risks posed by the database’s operational delays, citing recent incidents such as the cyberattack on Change Healthcare, which disrupted the healthcare industry for weeks.
On May 8, CISA announced the launch of its Vulnrichment program to enhance vulnerability metadata. MITRE, which oversees the CVE program, also approved new guidelines for organizations assigning CVEs. Dozens of cybersecurity experts signed the letter to Congress and Secretary Raimondo, calling the NVD “critical infrastructure for numerous cybersecurity products” and emphasizing the urgency of its funding and protection.


