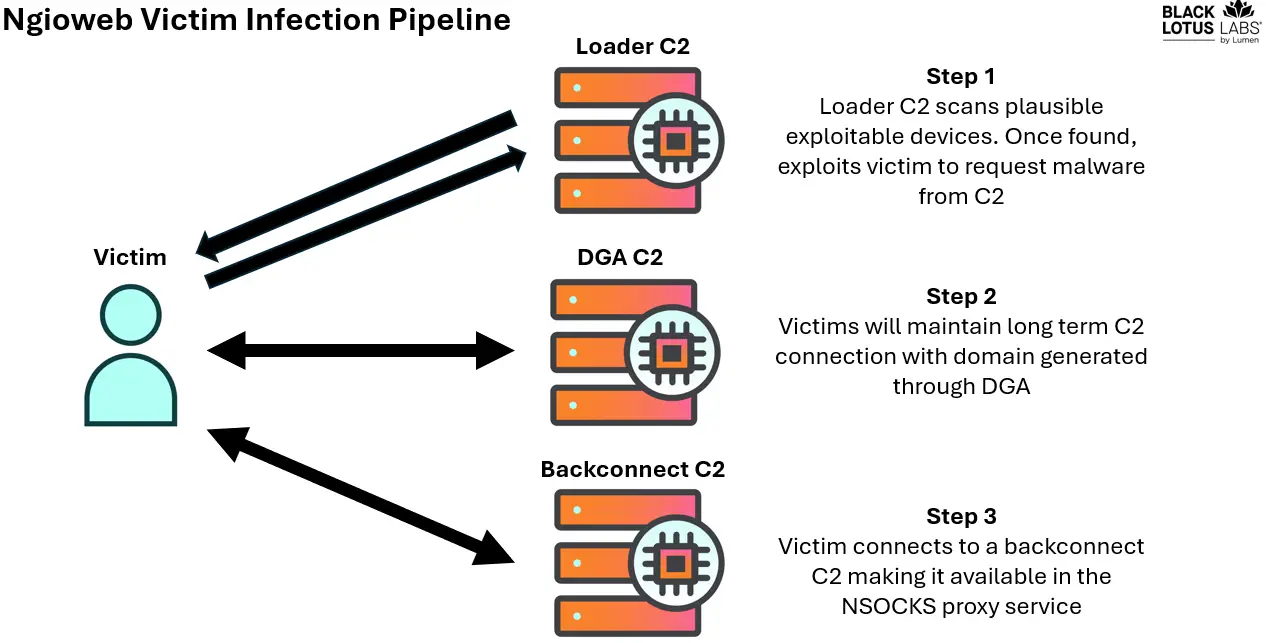
ngioweb botnet infection chain
The Black Lotus Labs team at Lumen Technologies has unveiled a sophisticated operation behind the ngioweb botnet, which serves as the backbone for one of the largest criminal proxy services, NSOCKS. This service leverages approximately 35,000 bots daily across 180 countries, with 60% of these located in the United States.
Investigations revealed that nearly 80% of NSOCKS bots are linked to the ngioweb botnet, which targets IoT devices and SOHO routers. Through this infrastructure, malicious actors obfuscate harmful traffic, conduct phishing campaigns, and orchestrate DDoS attacks.
Lumen Technologies successfully identified over 180 command-and-control (C2) servers used to anonymize users. These servers not only sustain the NSOCKS operation but also enable various criminal groups, including Shopsocks5, to exploit the botnet’s infrastructure.
An analysis of ngioweb revealed its reliance on numerous exploits targeting vulnerable devices, although it does not employ zero-day vulnerabilities. Instead, the botnet operators focus on outdated firmware versions and legacy software.
One of the primary risks posed by ngioweb is the concurrent use of infected devices by multiple criminal groups. Lumen Technologies has blocked all traffic associated with the ngioweb botnet on its network and has published Indicators of Compromise (IoCs) to aid other organizations in combating this threat.
Beyond standard proxy functions, NSOCKS enables attackers to configure domain-specific filters, including targeting “.gov” and “.edu” domains. This capability facilitates tailored attacks on government entities and educational institutions. The botnet’s architecture supports prolonged activity, with up to 40% of infected devices remaining compromised for over a month.
To mitigate this threat, experts recommend regularly updating router firmware, avoiding default passwords, and securing administrative interfaces. Organizations should actively block suspicious IP addresses and implement enhanced security measures to prevent attacks.
The findings underscore the growing popularity of proxy botnets among cybercriminals, emphasizing the need for robust collaboration and coordinated efforts across the cybersecurity industry.


