In June, HP specialists uncovered a phishing campaign targeting users in France, wherein artificial intelligence was employed to generate malicious code. The primary aim of the attack was the dissemination of AsyncRAT. The researchers detailed their findings in the second-quarter 2024 threat report.
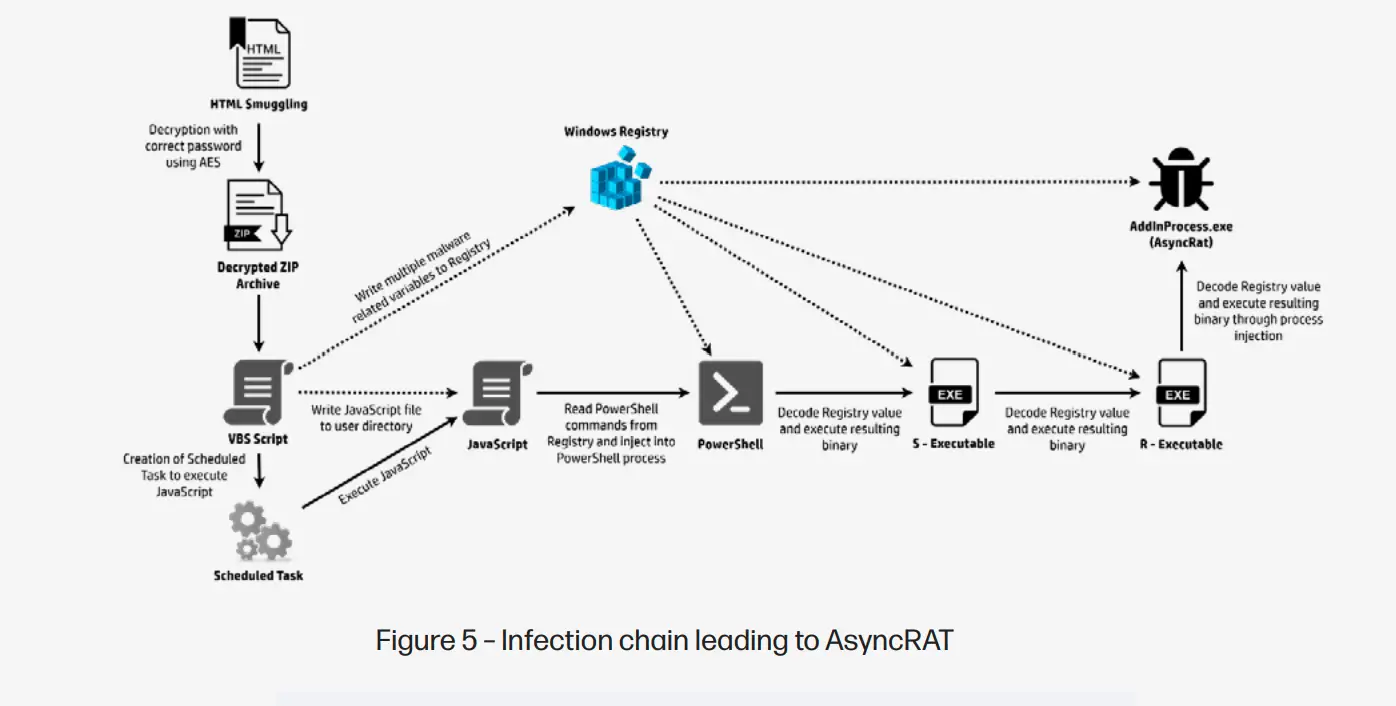
The attackers employed the method of HTML Smuggling—a technique where password-protected archives are transmitted via HTML documents. Malefactors embedded VBScript and JavaScript into these archives, which executed malicious actions on the compromised system. Experts deciphered the password and discovered code structured in a manner characteristic of generative AI. The entire code was annotated with comments meticulously explaining its functionality—a rarity in manually written malware.
HP specialists emphasize that such comprehensive comments in the code and the use of natural language for function and variable names are indicators that the code may have been generated by AI. Analysis revealed that the VBScript created tasks in the Windows Scheduler and modified the system registry to maintain its persistence.
In the subsequent stage of the attack, AsyncRAT—an open-source malware providing the hacker with remote access to the infected system, allowing for keystroke interception and the execution of additional malicious commands—was downloaded and executed. The HP report also notes that this type of archive became the most prevalent method for delivering malware in the first half of 2024.
Another case emerged as one of the most notable examples of malware utilization in web browsers: ChromeLoader. This program hijacks the victim’s browser session and redirects requests to sites controlled by the attackers. In the second quarter of 2024, campaigns distributing ChromeLoader became more extensive and meticulously planned. The malware was disseminated through advertisements leading to sites offering PDF converters. Functional applications concealed malicious code within MSI files, and the use of valid digital signature certificates aided in circumventing Windows security mechanisms, thereby increasing the likelihood of a successful attack.
During the investigation of attacks in the second quarter, specialists also identified a campaign where SVG files were employed to propagate malware. This format is widely used in graphic design and supports numerous features, including scripts. Cybercriminals exploited the capability to embed malicious JavaScript scripts into images, leading to attempts to infect victims’ devices with various information stealers.
The use of generative AI significantly simplifies the development of malicious code, enabling less experienced attackers to craft complex attacks within minutes. Such technologies not only expedite the creation of malware but also allow for customization targeting specific objectives, whether Linux or macOS platforms or particular regions. Even if AI is not utilized to create fully-fledged malware, it plays a pivotal role in the development of advanced threats, which grow increasingly sophisticated with each passing day.


