Cybersecurity experts from the QiAnXin Cyber Intelligence Center have reported the discovery of a new threat posed by the APT-Q-12 group, also known as “Pseudo Hunter.” This cyber-espionage group, rooted in Northeast Asia, targets governments and corporations across East Asia, including China, North and South Korea, and Japan.
The group’s activities were first brought to light in 2021 when QiAnXin experts published a detailed technical report. However, traces of their attacks can be tracked back to 2017, with connections to the actions of the infamous Darkhotel group.
Following 2019, the activity associated with Darkhotel began to wane, leading to the emergence of new cyber-espionage groups such as APT-Q-11, APT-Q-12, APT-Q-14, and others. These groups, employing various tactics and methods, focused on targeting governmental and corporate entities. Specialists have determined that many of these groups are continuations or offshoots of Darkhotel’s operations.
The primary method of espionage for APT groups, including APT-Q-12, involves the use of sophisticated plugins, enabling attackers to swiftly and efficiently extract critical data from targeted systems. For instance, in one operation codenamed “ShadowTiger,” plugins were used to scan the file structure and upload documents to the attackers’ servers.
APT-Q-12 pays particular attention to gathering information about victims’ behavior, employing well-crafted phishing techniques and embedding spyware in popular email and office applications. The group develops and deploys various types of malware tailored to specific platforms, whether desktop computers, mobile devices, or corporate servers.
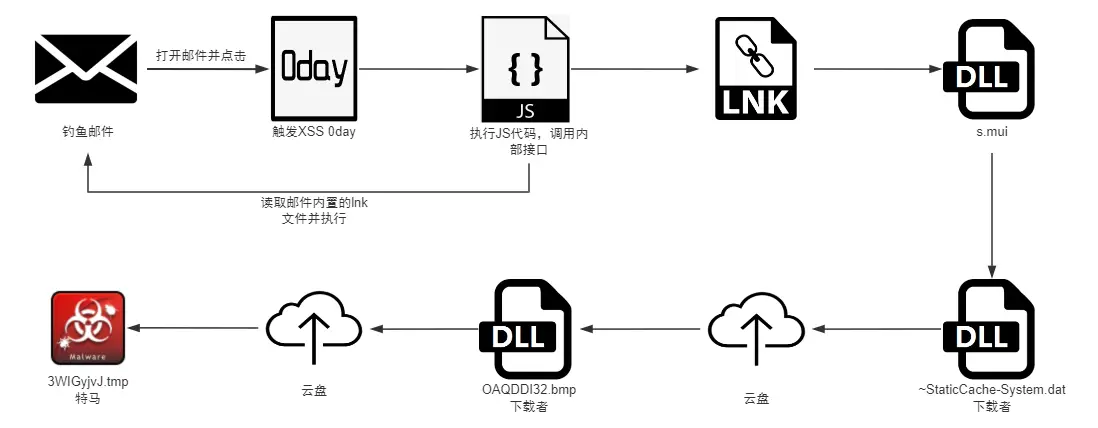
One of the most significant discoveries by cybercriminals was the identification of zero-day vulnerabilities in email clients on the Windows platform. APT-Q-12 utilizes advanced attack methods that involve executing malicious code through vulnerabilities in browsers and email applications, allowing them to infiltrate systems and establish control.
During the analysis, several types of malware were identified, among which a trojan stood out. This trojan is installed on the system through a chain of actions involving scripts and specialized commands. It is designed to capture and transmit confidential information, making it a potent tool in the hands of attackers.
APT-Q-12 also employs plugins to capture keystrokes and gather information about user activities, enabling them to monitor daily activities and uncover valuable data such as passwords and other credentials. These data are then encrypted and transmitted to the attackers’ servers for further analysis and exploitation.
To mitigate such threats, experts recommend using modern EDR systems that can effectively detect and prevent attacks at early stages. Contemporary cybersecurity solutions based on cyber intelligence data are becoming increasingly essential as threats in the East Asian region continue to escalate.
APT-Q-12 continues to evolve its attack methods, posing a serious threat to the security of nations and corporations in the region. Experts remain vigilant in monitoring their activities and refining protective measures to minimize the damage from potential attacks.


