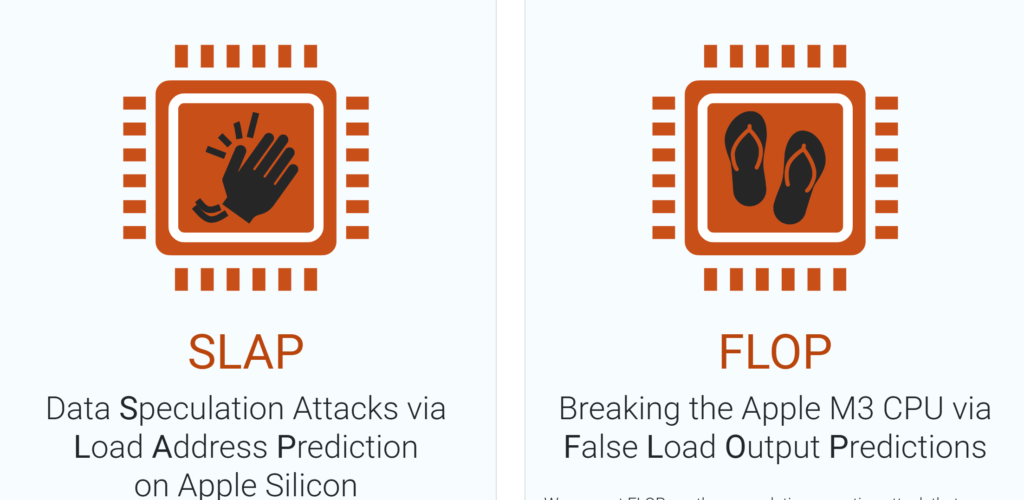
Researchers from the Georgia Institute of Technology and Ruhr University Bochum have uncovered two new side-channel attacks targeting Apple processors—SLAP and FLOP. These exploits take advantage of vulnerabilities in speculative load prediction mechanisms embedded in the latest generations of Apple Silicon chips, beginning with M2/A15 and M3/A17.
SLAP (Speculative Load Address Prediction) exploits the Load Address Predictor (LAP), a component that enhances CPU performance by anticipating which data will be needed in the near future. However, when predictions go awry, the processor performs speculative computations on data that should remain inaccessible. This flaw enables attackers to extract sensitive information, such as email content and browsing history from Safari.
FLOP (False Load Output Prediction) targets the Load Value Predictor (LVP) embedded in Apple M3/A17 processors. This mechanism predicts memory values before they are officially retrieved, accelerating computational efficiency. However, flawed predictions allow attackers to bypass critical security checks, potentially exposing highly sensitive data, including location history, calendar entries, and credit card details.
The researchers showcased real-world demonstrations of these vulnerabilities. In one attack scenario targeting Safari, an adversary executed malicious JavaScript to gain unauthorized access to the contents of a Proton Mail inbox that was open in an adjacent browser tab. In another experiment using an M3 processor, researchers successfully extracted text from a Harry Potter novel, despite the book never being explicitly requested by the program.
Apple has not yet released official patches, though the company is expected to address these vulnerabilities in upcoming software updates. In the meantime, users are advised to limit the use of JavaScript-enabled web browsers and stay vigilant for security updates to mitigate potential threats.