Cybercriminals have discovered a method to bypass phishing protection in iMessage, which blocks links in messages from unknown senders. By deceiving users into responding to such messages, the attackers reactivate the links and disable the built-in security features.
SMS phishing targeting mobile devices is becoming increasingly prevalent. To mitigate such attacks, iMessage automatically disables links in messages from unidentified senders. However, if a user replies to the message or adds the sender to their contacts, the protection is removed.
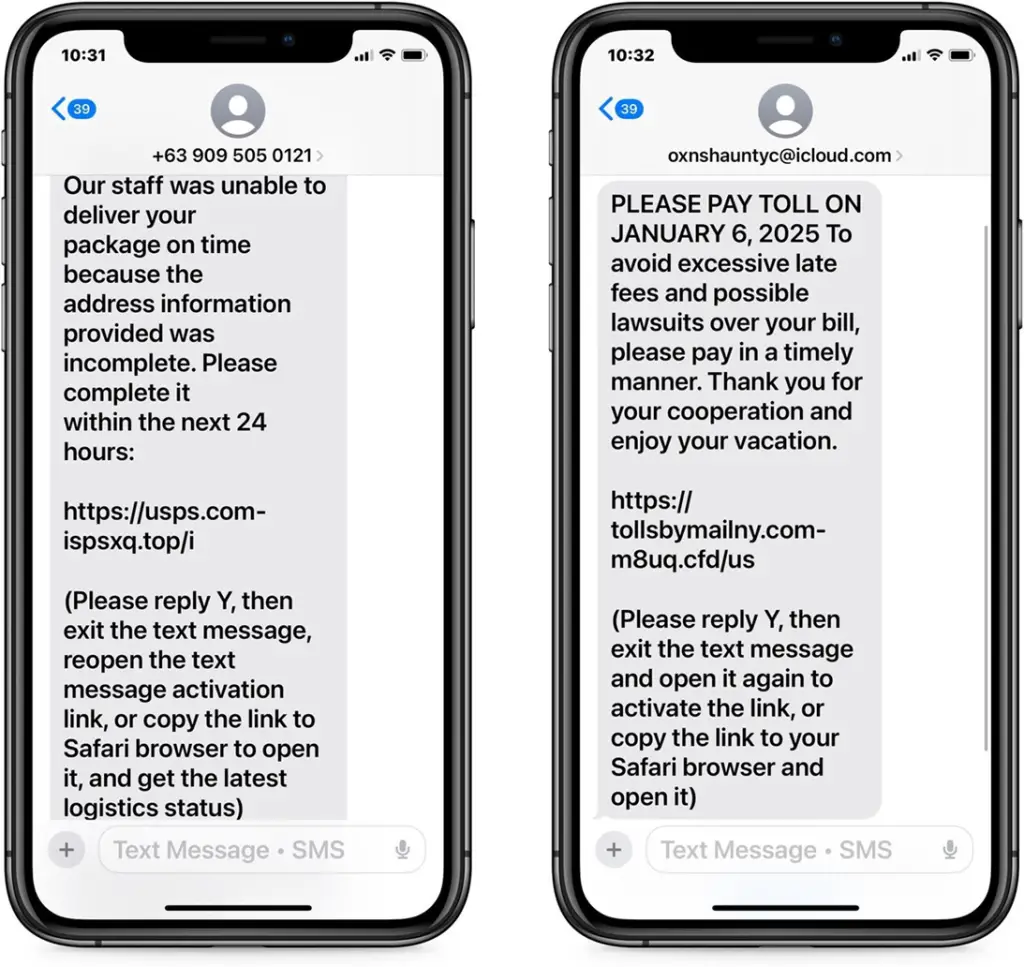
Recently, there has been a surge in attacks where scammers, posing as representatives of major services, urge victims to respond to messages to reactivate blocked links. These messages are often disguised as notifications about delivery issues or unpaid fines. For example, users may be prompted to reply “Y” to access a link.
This tactic exploits users’ habits of responding with “Yes” or “Stop” to service-related messages. A response not only reactivates the link but also informs the attackers that the message has reached an active recipient, increasing the likelihood of further attacks. Elderly individuals are particularly vulnerable, as they may fail to recognize the deception and inadvertently share sensitive information, such as bank card numbers.
Experts strongly advise against responding to messages with disabled links or fulfilling requests from unknown senders. Instead, users should directly contact the organization purportedly responsible for the message to verify its authenticity.