Security researchers at Netlify have identified a large-scale campaign exploiting cloud infrastructure for covert cryptocurrency mining. The operation, which persisted from September to November 2024, affected numerous cloud services, including Microsoft, ProtonVPN, and other major providers. The attackers leveraged thousands of fraudulent accounts, distributed across hundreds of domains and IP addresses, to obtain free computational resources.
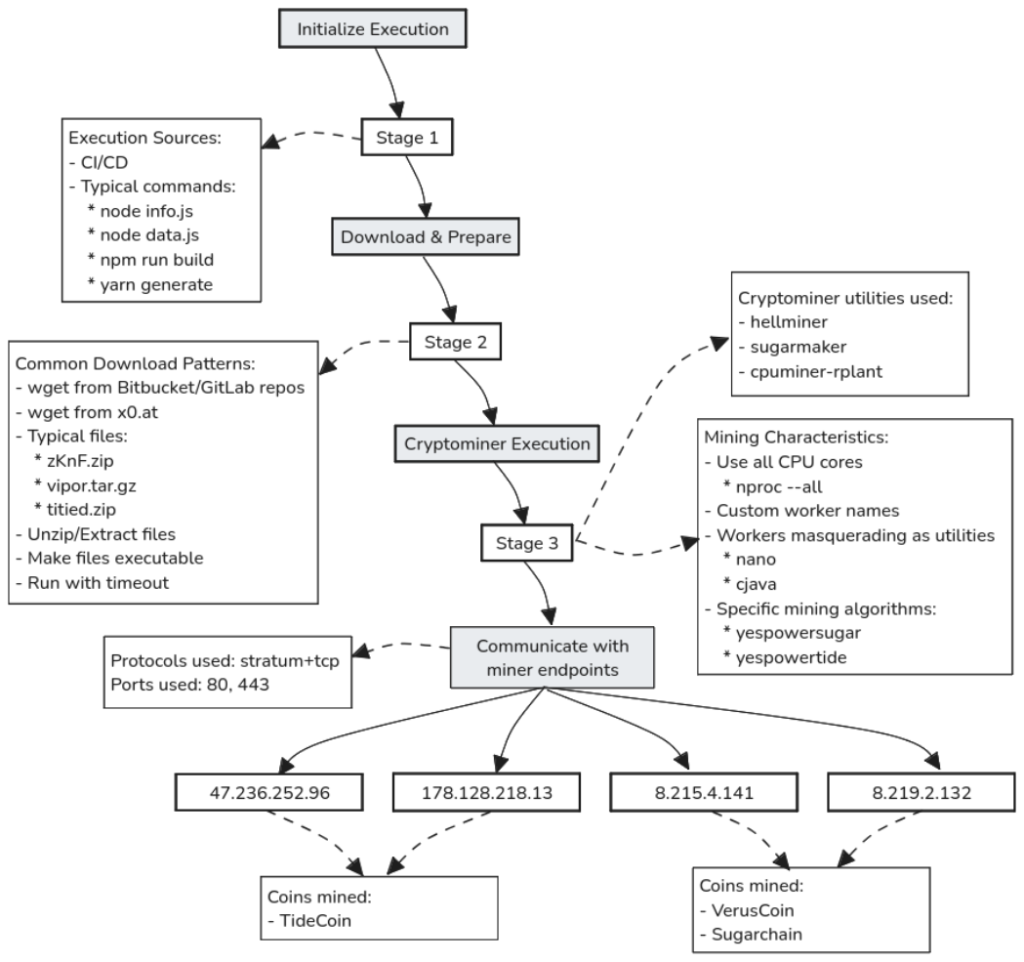
According to investigators, the attack relied on deploying and executing malicious mining binaries, specifically targeting CPU-based cryptocurrency mining. Initially, the attackers focused on TideCoin before shifting to VerusCoin. Over the course of the campaign, funds were funneled into seven cryptocurrency wallets, accumulating approximately $6,500. However, the actual financial impact on cloud service providers is estimated to be in the tens of thousands of dollars due to the extensive consumption of cloud resources.
The attackers employed sophisticated evasion techniques, frequently modifying their execution strategies. Researchers uncovered at least eight variations of malicious scripts, which were deployed through CI/CD pipelines and executed on cloud provider servers. The highest concentration of fraudulent accounts originated from Microsoft Cloud IP addresses (over 2,400 cases), with additional activity traced to Telkom Indonesia, ProtonVPN, and Datacamp.
Further analysis revealed that the attackers leveraged mass account registration tactics, utilizing email address manipulation techniques such as “Plus Addressing” and “Subdomain Addressing.” In total, researchers identified over 3,200 such addresses, with the majority linked to six privately registered domains, created between 2023 and 2024.
Technical investigations indicated that the attackers utilized Bitbucket and GitLab to host scripts responsible for downloading and executing the malicious payloads. The mining operations were conducted on servers within networks belonging to Alibaba Cloud, DigitalOcean, and other providers. In total, four IP addresses were identified as part of the campaign.
Netlify’s experts emphasize that this operation dates back to 2021, but has seen a significant resurgence in recent months. The perpetrators specifically targeted the SaaS industry, exploiting free-tier cloud services for unauthorized mining activities. Organizations are advised to strengthen cloud activity monitoring, scrutinize outbound traffic, and proactively block suspicious IP addresses associated with this campaign.