AmberWolf researchers have uncovered vulnerabilities in the VPN clients SonicWall NetExtender and Palo Alto Networks GlobalProtect, collectively named NachoVPN. These flaws enable attackers to deploy malicious updates when clients connect to rogue VPN servers, typically facilitated through phishing sites or counterfeit documents.
By leveraging fake servers, attackers can steal user credentials, escalate privileges to Root or SYSTEM levels, install malware via fraudulent updates, forge code signatures, or conduct Man-in-the-Middle (MiTM) attacks by injecting malicious root certificates.
The researchers focused primarily on SSL-VPN clients and Zero Trust solutions, widely adopted in corporate environments. Their analysis revealed that the vulnerabilities stem from excessive client trust in servers and minimal interaction required for a successful attack.
To demonstrate these attack scenarios, AmberWolf developed NachoVPN, an open-source tool serving as a proof-of-concept (PoC). It simulates the behavior of malicious VPN servers exploiting the identified vulnerabilities.
NachoVPN supports several popular corporate VPN products, including Cisco AnyConnect, SonicWall NetExtender, Palo Alto GlobalProtect, and Ivanti Connect Secure. Its capabilities include tailoring attacks to specific VPN clients and extending functionality to incorporate additional vulnerabilities.
The release of NachoVPN is accompanied by detailed advisory reports on the discovered vulnerabilities, including:
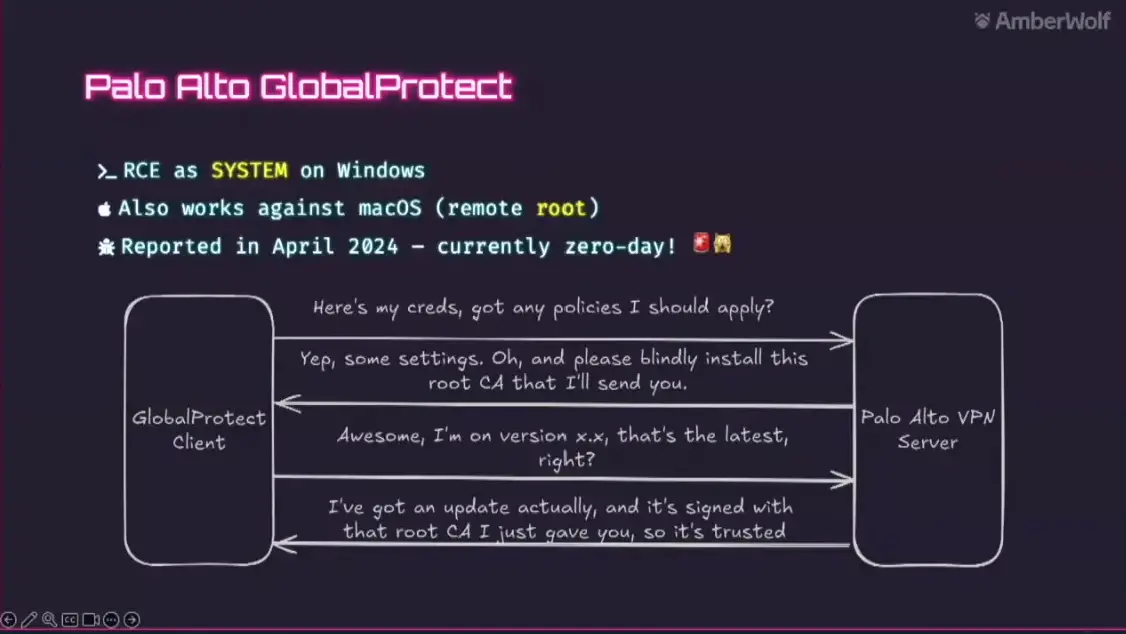
- CVE-2024-5921 (CVSS score: 5.6) in Palo Alto GlobalProtect, allowing remote code execution and privilege escalation.
- CVE-2024-29014 (CVSS score: 8.8) in SonicWall SMA100 NetExtender for Windows, enabling SYSTEM-level code execution through client updates.
The study also simulated real-world attacks in corporate environments, illustrating how VPN client vulnerabilities can grant attackers control over end-user devices.
SonicWall advises upgrading to NetExtender version 10.2.341 or later to mitigate the vulnerability. Palo Alto Networks recommends using the VPN client in FIPS-CC mode to reduce attack risks, although full protection requires updating to GlobalProtect version 6.2.6 or newer.
To safeguard networks, researchers urge organizations to review AmberWolf’s published technical reports. These documents provide detailed insights into attack vectors and practical recommendations for mitigating potential threats.


