A new remote access trojan (RAT) named MoonPeak was uncovered in a cyber group’s campaign linked to the North Korean government. Cisco Talos experts have attributed this malicious campaign to the hacker group UAT-5394, which they believe has tactical overlaps with the well-known nation-state actor codenamed Kimsuky.
MoonPeak, currently under active development, is a variant of the notorious Xeno RAT malware, previously employed in phishing attacks. These attacks aimed to deliver payloads from cloud services such as Dropbox, Google Drive, and Microsoft OneDrive, all managed by the threat actors. Among the key features of Xeno RAT are the capabilities to download additional plugins, manage processes, and communicate with a command and control (C2) server.
The resemblance between these two intrusion toolkits suggests that UAT-5394 may either be Kimsuky itself (or a subdivision thereof) or another group within North Korea’s cyber division utilizing Kimsuky’s tools.
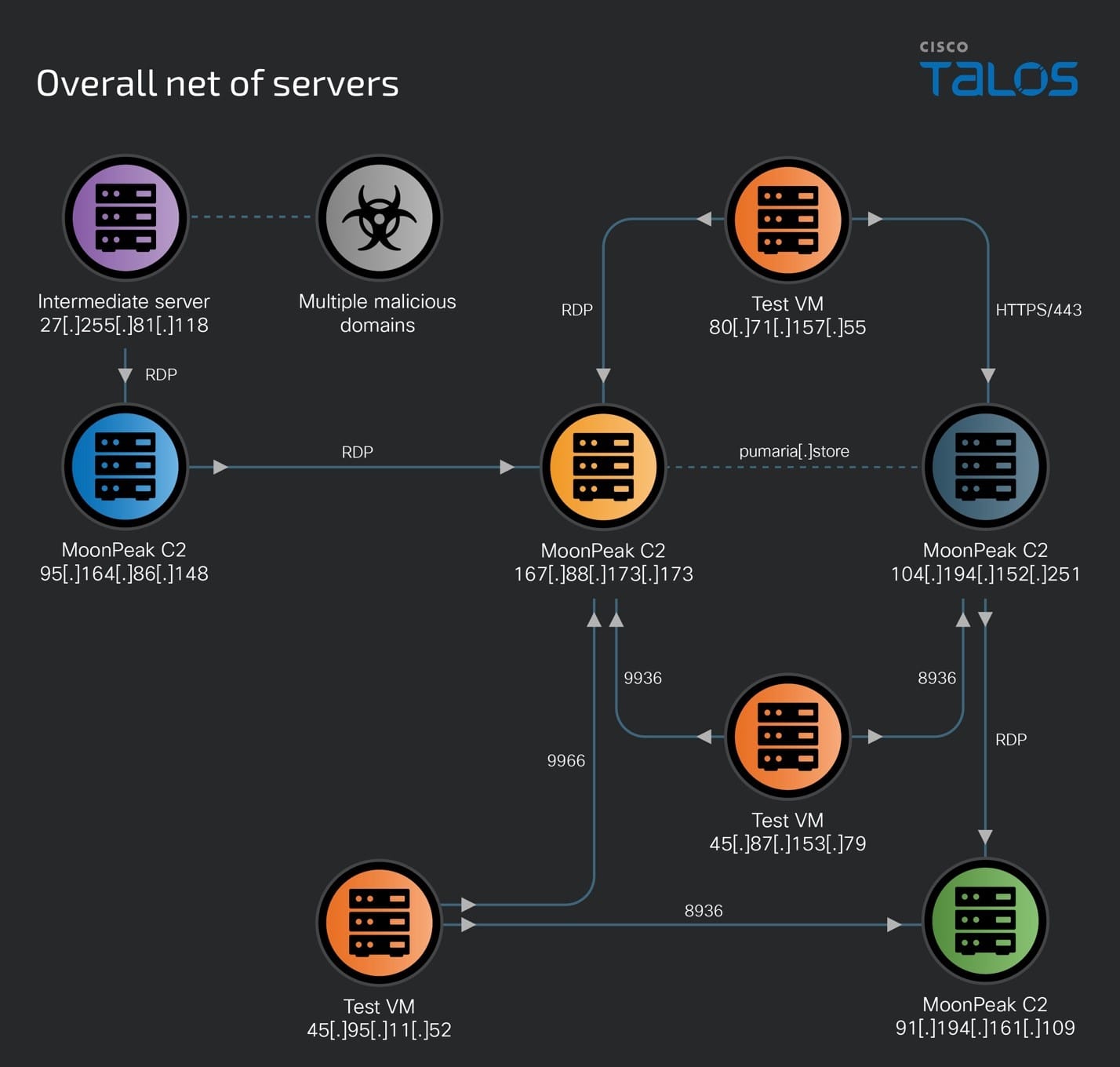
A central element of this campaign is the deployment of new infrastructure, including C2 servers, malware-hosting websites, and test virtual machines. This infrastructure has been purpose-built to support the new versions of MoonPeak.
Talos researchers noted that the C2 servers store malicious artifacts used to create and maintain the new infrastructure. In several instances, the attackers were observed accessing existing servers to update payloads and extract information gathered by MoonPeak.
The shift from utilizing legitimate cloud storage to deploying their own infrastructure underscores a change in the hackers’ approach. However, the objectives of the current campaign remain unknown.
It is important to note that the “continuous evolution of MoonPeak is closely tied to the creation of new infrastructure by the threat actors,” and each new version of the malware incorporates novel evasion techniques and alterations in communication mechanisms to prevent unauthorized access.
The researchers also highlighted that the hackers ensured compatibility between specific versions of MoonPeak and certain C2 server variants. The rapid development of new tools and infrastructure indicates the group’s intention to swiftly expand the campaign and establish more access points and C2 servers.


