Experts at Knownsec 404 have uncovered a series of new attacks in which threat actors used documents containing information about military installations to deceive victims into opening them and inadvertently granting remote access to their devices.
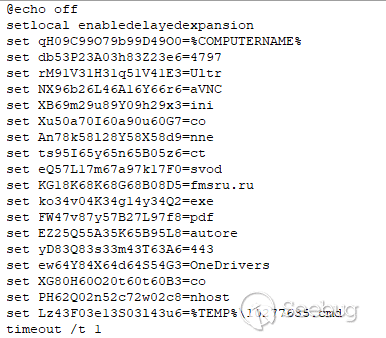
The primary attack vector involved the use of self-extracting 7Z archives (SFX) to deploy malware. The attackers leveraged UltraVNC, disguising it as legitimate system processes. The lure for victims consisted of documents detailing the status and locations of military facilities.
Inside the archives were scripts designed to install additional files. These scripts were encrypted to complicate analysis and executed tasks such as extracting and running supplementary components, including UltraVNC configurations. The malware connected to remote servers via port 443, enabling attackers to clandestinely control compromised devices.
The attacks bear similarities to those attributed to the Gamaredon group, but the attribution and tactics suggest a different actor—GamaCopy. This group focuses on targeting Russian defense and infrastructure entities while mimicking Gamaredon’s methods. The key differences between the two groups lie in the language of the bait documents and the installation techniques. Gamaredon predominantly uses Ukrainian-language documents, while GamaCopy employs Russian-language materials. Additionally, GamaCopy utilizes alternative connection ports and more advanced encryption techniques.
Experts highlight that the use of open-source tools and the imitation of other groups’ attack methods allow these threat actors to obscure their tracks. This not only complicates detection but can also mislead even seasoned cybersecurity professionals. The attackers aim not only to collect intelligence but also to sow chaos and confusion within enemy systems.


