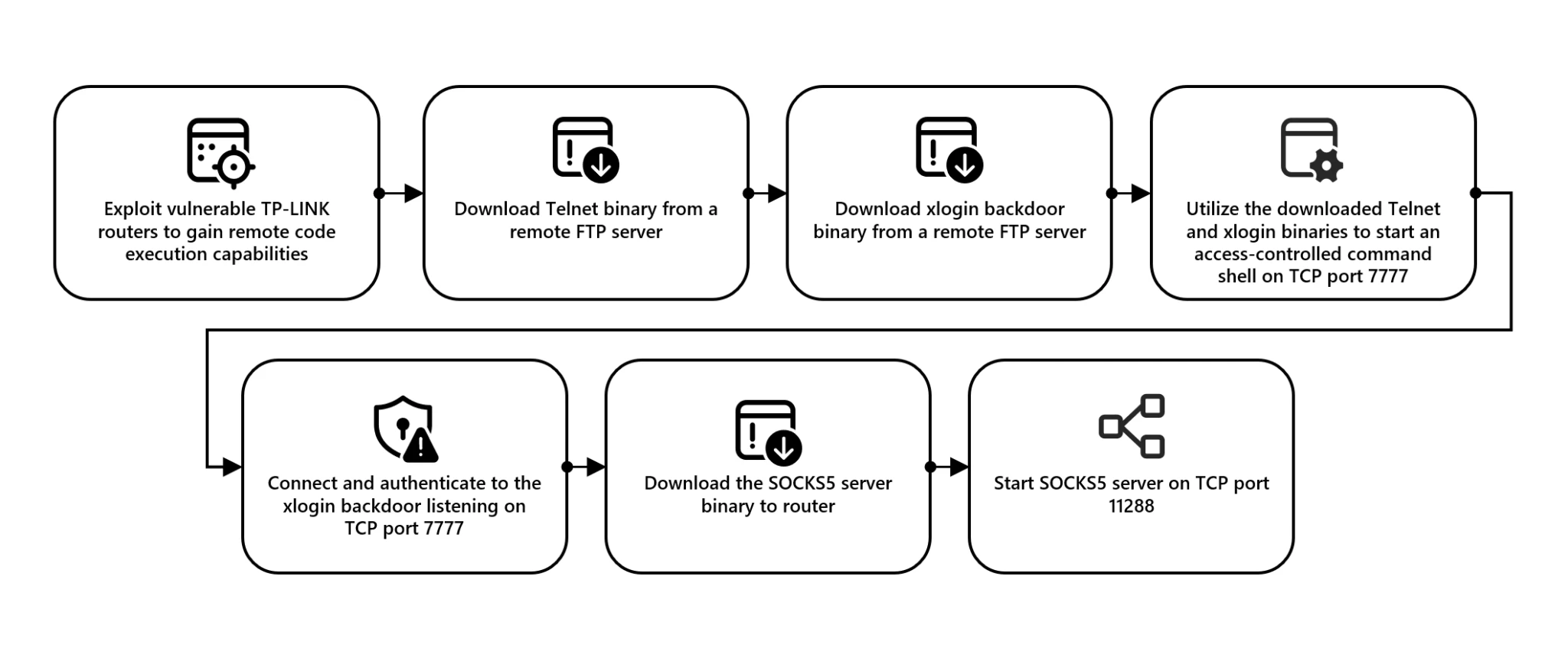
Microsoft recently reported a new threat posed by Chinese hackers who are exploiting an extensive network of compromised TP-Link routers and other internet-connected devices to launch attacks on Azure cloud service users. This network, known as CovertNetwork-1658, actively employs password-spraying attacks—attempts to breach accounts by conducting mass login attempts from various IP addresses, thereby circumventing security systems.
CovertNetwork-1658, comprising up to 16,000 hacked devices, was first identified by researchers in October 2023. A unique aspect of the network is its use of port 7777 to control infected devices, which has led to its designation as Botnet-7777. According to Microsoft, several Chinese hacking groups are leveraging the network to compromise Azure accounts, posing a significant security risk across various sectors.
Experts estimate that CovertNetwork-1658 uses hundreds of IP addresses with a short lifespan—approximately 90 days. This obfuscates detection efforts, as each IP address performs a limited number of login attempts, reducing the likelihood of exposure.
A critical component of this attack is the botnet’s support infrastructure, which enhances the chances of successfully breaching accounts. Microsoft noted that compromised data is rapidly shared between CovertNetwork-1658 and affiliated hacker groups, such as Storm-0940. This group specifically targets institutions in North America and Europe, including think tanks, governmental bodies, and defense organizations.
Once network access is gained, attackers employ lateral movement, enabling them to install additional malware and exfiltrate data.
Microsoft also highlighted the challenges of detecting such attacks. Key methods used to evade security systems include:
- Utilizing compromised IP addresses from residential routers;
- Rotating IP addresses to create the illusion of numerous distinct sources;
- Limiting the volume of password-guessing attempts to avoid triggering monitoring systems.
While recent activity from CovertNetwork-1658 has declined, this does not indicate its cessation. Microsoft believes the network is expanding its infrastructure and altering digital signatures to bypass previously identified defenses.
Experts recommend periodically rebooting devices, as most do not retain malware post-restart. However, this does not prevent reinfection.


