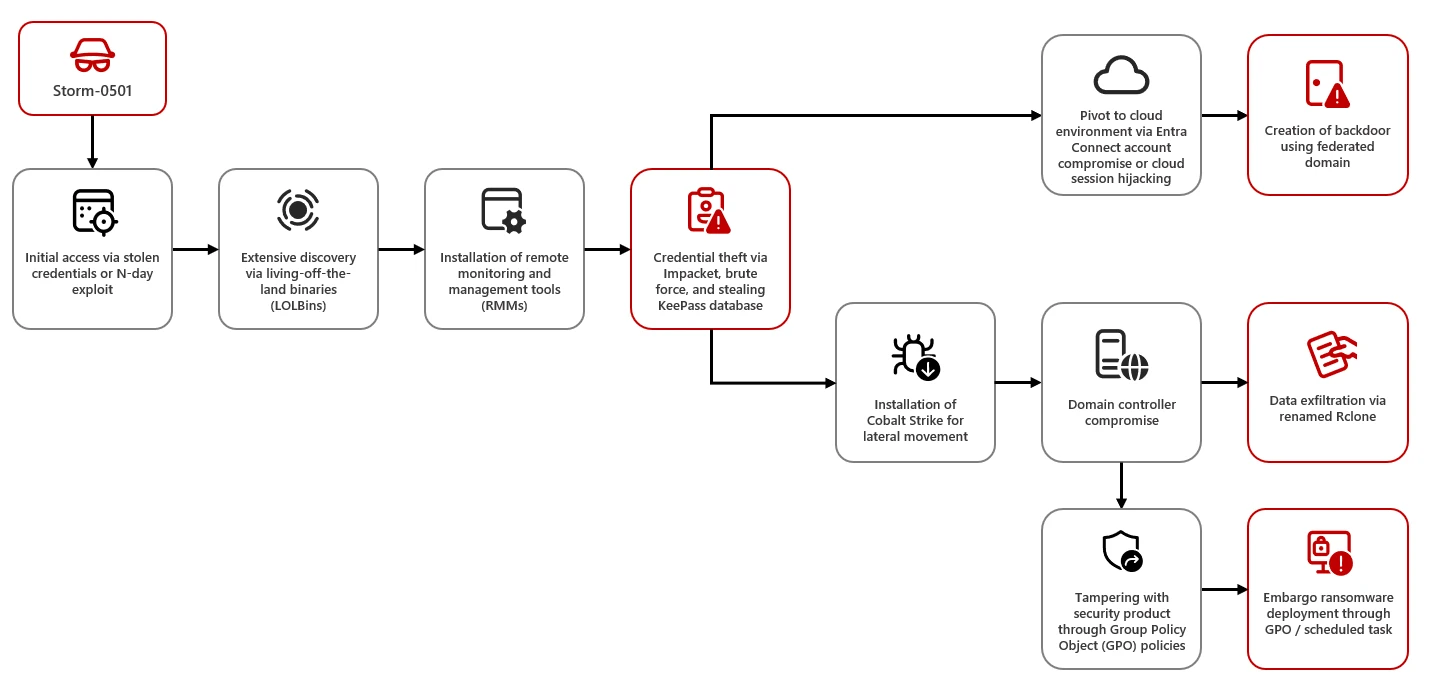
Microsoft has identified a new hacker group, tracked under the identifier Storm-0501. Previously, this group collaborated with notorious ransomware gangs such as Hive, BlackCat (ALPHV), Hunters International, LockBit, and Embargo. Now, however, Storm-0501 has transitioned to operating independently, targeting hybrid cloud environments and utilizing open-source tools for their attacks. The primary objective of these cybercriminals is financial gain.
Recently, Storm-0501 executed multi-stage attacks within the United States, breaching hybrid cloud environments and spreading from local devices to the cloud. These attacks resulted in credential theft, exfiltration of sensitive information, system tampering, creation of backdoors, and the deployment of ransomware. The group’s victims have included government entities, manufacturing firms, transportation services, law enforcement agencies, and even hospitals.
It is known that Storm-0501 has been active since at least 2021. In their operations, the group employed several types of ransomware developed and maintained by other threat actors. To gain initial access, the criminals typically leverage stolen credentials and known vulnerabilities to compromise accounts with elevated privileges. Once these privileges are obtained, the hackers pivot to the cloud, exploiting vulnerabilities in the interfaces between environments.
A recent report by Microsoft Threat Intelligence highlights that as the use of hybrid cloud environments expands, securing resources across multiple platforms is becoming an increasingly complex challenge. In one of the latest attacks, Storm-0501 exploited known vulnerabilities in Zoho ManageEngine, Citrix NetScaler, and ColdFusion 2016, exposing the inadequate security measures of the affected organizations.
During the attack, Storm-0501 uses standard Windows tools and commands such as “systeminfo.exe,” “net.exe,” “nltest.exe,” and “tasklist.exe,” alongside open-source reconnaissance and remote management utilities like AnyDesk. Upon obtaining administrative rights, the group steals credentials to move laterally within the network and ultimately reach the domain controller to deploy ransomware.
Once Storm-0501 seizes control of the network and moves into the cloud environment, they deploy a new ransomware called Embargo, built using Rust and employing advanced encryption techniques. However, the attackers do not always resort to ransomware; in some cases, they simply maintain persistent access to the network.
Microsoft is diligently working to enhance the security of its Microsoft Entra ID service (formerly Azure AD), which has been exploited by these attackers for credential theft. The tech giant advises organizations to implement robust authentication mechanisms, limit access for synchronization accounts, and employ EDR solutions to strengthen security.


