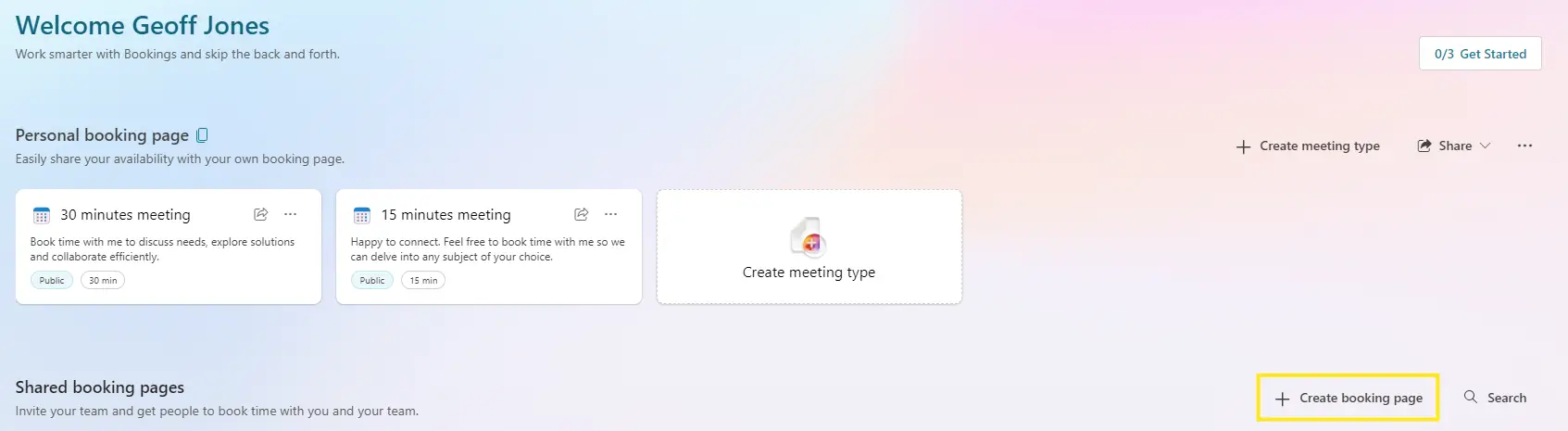
The option to create a shared Bookings page
Microsoft Bookings, one of the popular features in Microsoft 365, poses a potential security risk for companies, as it allows users to create Entra accounts without requiring administrative privileges. According to Cyberis, this capability opens doors for malicious actors who may establish a fake account disguised as a legitimate employee, using it to launch internal phishing attacks or manipulate external partners.
If an attacker gains access to an employee’s Microsoft 365 account, they can exploit the shared booking pages feature to impersonate influential figures within the company, such as the CEO or financial manager. This allows the attacker to deceive employees and potentially orchestrate fraudulent fund transfers.
One notable feature of Bookings is the ability to create “special” email addresses within the domain, such as “admin@” or “hostmaster@.” This enables attackers to conduct advanced social engineering attacks aimed at seizing control over infrastructure. Such tactics make detection significantly more challenging and may bypass identity spoofing protections built into Microsoft.
Moreover, an attacker creating a booking page can establish an account that matches the email address of a former employee. This tactic allows interception of incoming messages to that address and even password resets for external services.
It’s worth noting that these mailbox accounts do not require Microsoft 365 licenses and can remain active without incurring costs for the company. Such hidden accounts can only be detected via PowerShell and remain invisible within the Exchange Admin Center.
To mitigate these risks, security experts recommend disabling the ability for regular users to create shared booking pages, as well as conducting an audit of existing hidden mailboxes. It is essential to regularly review access rights and monitor for new account creations in Entra.
These actions can reduce the vulnerability of companies to such attacks and strengthen the protection of sensitive information, especially against phishing attacks and fraud.


