Experts from Kaspersky Lab have reported a new wave of targeted cyberattacks carried out by the SideWinder group. According to the company, the attackers are using a new espionage tool—StealerBot—focusing on large organizations and strategic infrastructure in the Middle East and Africa.
The cyber group SideWinder, also known as T-APT-04 or RattleSnake, was first detected by cybersecurity specialists in 2012 and has remained one of the most active groups worldwide. In 2018, Kaspersky Lab reported on its activities. The primary targets of the group’s attacks have been military and government institutions in Pakistan, Sri Lanka, China, and Nepal, as well as companies and organizations from other South and Southeast Asian countries.
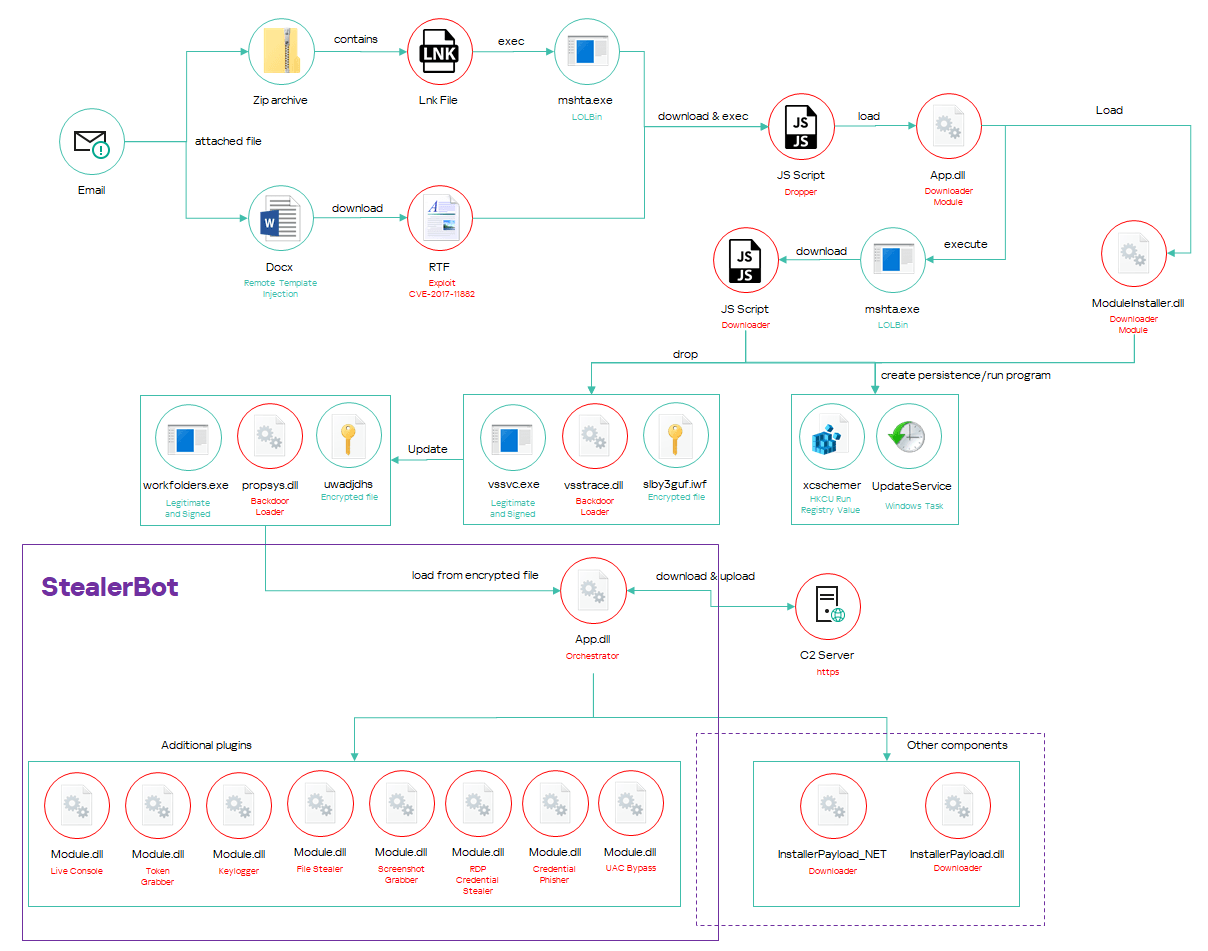
For their attacks, SideWinder has used malicious documents that exploited vulnerabilities in Microsoft Office applications. In some cases, other file formats such as LNK, HTML, and HTA were employed, which the attackers distributed in the form of archives. To entice victims into opening the malicious files, these documents often contained information from popular websites, giving them an air of legitimacy. During its cyberattacks, the group employed several families of malware, including both specially developed and modified versions of off-the-shelf programs, along with publicly available RAT trojans.
What has changed: SideWinder has expanded the scope of its attacks, now targeting organizations in the Middle East and Africa. Furthermore, the group has introduced a new espionage tool—StealerBot. This advanced implant was specifically designed for conducting surveillance operations. Currently, StealerBot is the group’s primary tool following the exploitation of vulnerabilities.
StealerBot is capable of executing numerous tasks, such as deploying additional malware, taking screenshots, logging keystrokes, stealing browser passwords, intercepting RDP (Remote Desktop Protocol) credentials, and extracting files.
As noted by the company, StealerBot allows attackers to monitor systems while remaining extremely difficult to detect. The program is built on a modular structure, with each component responsible for a specific task. These modules are not stored as files on the hard drive, making them even harder to trace: all elements are loaded directly into memory. A key role in StealerBot’s operation is played by the so-called “Orchestrator”—the central component that oversees the entire operation, communicates with the attackers’ command server, and coordinates the actions of all program modules.


