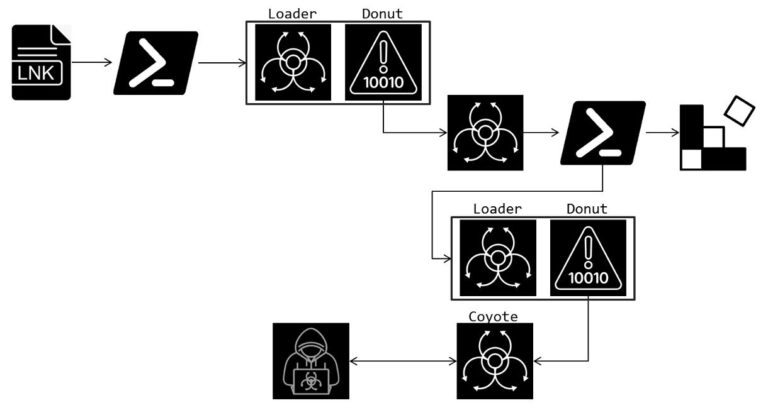
Ivanti has released security updates addressing several critical vulnerabilities in its Cloud Services Application (CSA) and Connect Secure products. These flaws could enable privilege escalation and arbitrary code execution.
The most severe of these is CVE-2024-11639, carrying a maximum CVSS score of 10.0. This vulnerability allows remote attackers to gain unauthorized administrative access to the web console. It affects Ivanti CSA versions prior to 5.0.3.
Other critical issues include CVE-2024-11772 and CVE-2024-11773, both rated 9.1 on the CVSS scale. These vulnerabilities permit command execution and SQL injection if an attacker possesses administrative credentials.
Another flaw, CVE-2024-11633, enables arbitrary code execution via argument injection in Ivanti Connect Secure versions below 22.7R2.4. A similar vulnerability, CVE-2024-11634, impacts both Connect Secure and Policy Secure, with each earning a CVSS score of 9.1.
Additionally, CVE-2024-8540 (CVSS 8.8) in Ivanti Sentry allows local attackers to modify sensitive application components due to insufficient permission enforcement.
Ivanti has resolved all these vulnerabilities in the following product versions: CSA 5.0.3, Connect Secure 22.7R2.4, Policy Secure 22.7R1.2, and Sentry versions 9.20.2, 10.0.2, and 10.1.0. The company stated that it is unaware of any active exploitation of these vulnerabilities.
Nevertheless, experts strongly urge users to promptly apply the updates. Past vulnerabilities in Ivanti’s products have been exploited by state-sponsored hackers, underscoring the critical importance of these patches in mitigating potential threats.