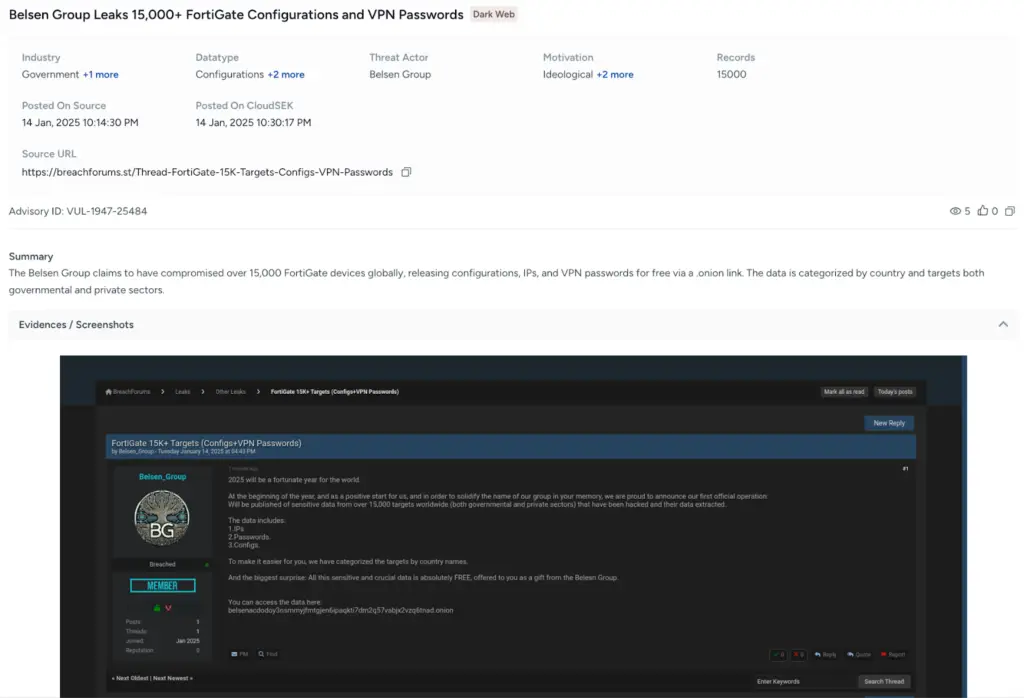
Threat actor leaking configs from over 15k Fortigate firewalls on their onion website for free
On January 15, cybersecurity researcher Kevin Beaumont reported a leak of configuration files and VPN information for 15,000 FortiGate devices. The exposed data included usernames, passwords (some in plaintext), device management certificates, and firewall configuration rules, all of which were published on the dark web.
According to a report by CloudSEK, the breach was orchestrated by a new hacking group known as the Belsen Group. The affected devices predominantly ran FortiOS versions 7.0.x and 7.2.x. Both CloudSEK and Beaumont concluded that the leak was linked to the exploitation of the Zero-Day vulnerability CVE-2022-40684 (CVSS score: 9.8), discovered in 2022. This flaw enabled attackers to bypass authentication through specially crafted HTTP or HTTPS requests.
The Belsen Group has been active in the cybercriminal sphere for several years. CloudSEK speculates that the group may have exploited the Zero-Day vulnerability as far back as 2022. The majority of the compromised data was harvested in October 2022, prior to the vulnerability being officially classified. Geographically, the breach impacted the United States, the United Kingdom, Poland, and Belgium, compromising over 20 organizations in these countries. Other affected nations include France, Spain, Malaysia, the Netherlands, Thailand, and Saudi Arabia.
Beaumont confirmed the authenticity of the breach by correlating IP addresses and device configurations using Shodan. The attack’s repercussions include:
- Exposure of sensitive credentials;
- Disclosure of firewall configurations, simplifying defenses’ circumvention;
- Compromise of digital certificates, enabling unauthorized access to devices.
Organizations are advised to take the following steps:
- Change all credentials, especially those identified in the leak;
- Inspect device configurations for vulnerabilities and strengthen access controls;
- Revoke and replace compromised digital certificates;
- Conduct audits and investigations to assess potential fallout from the 2022 compromise.
Meanwhile, Fortinet recently disclosed another Zero-Day vulnerability, CVE-2024-55591 (CVSS score: 9.8), affecting FortiGate devices running FortiOS versions 7.0.0–7.0.16 and 7.2.0–7.2.12. While this flaw is not directly connected to the Belsen Group attack, experts warn that attackers could exploit similar techniques.
Simultaneously, Arctic Wolf uncovered a large-scale campaign targeting FortiGate devices, which began in December 2024. Although no direct link to the data leak has been established, both Fortinet and Arctic Wolf have refrained from commenting on the situation.