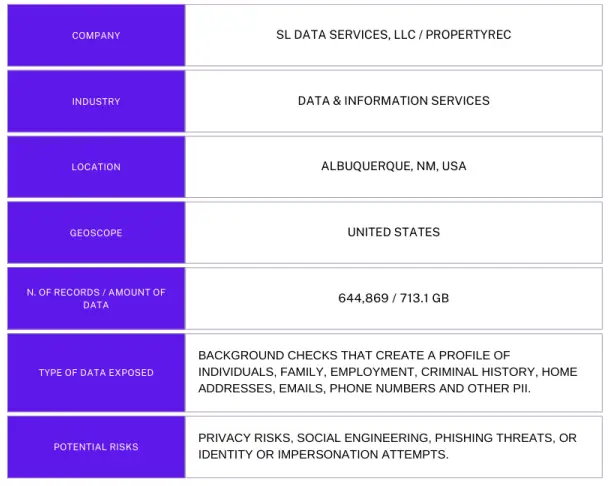
Jeremiah Fowler, a cybersecurity expert, reported the discovery of an unprotected database containing over 600,000 records belonging to SL Data Services, operating under the Propertyrec brand. The organization specializes in providing data on property owners and conducting background checks for criminal history.
The exposed database contained 644,869 PDF files with a total size of 713.1 GB, including court records, vehicle information (license plates and VINs), and reports on property owners. Approximately 95% of the documents examined by the researcher were labeled as “background checks.” These materials included full names (first, middle, and last), home addresses, phone numbers, email addresses, employment details, information on family members, social media accounts, and criminal records.
SL Data Services, an American company, operates a network of approximately 16 websites offering information services. One of these sites, Propertyrec, specializes in real estate data, as indicated by its mention within the database. Following notification of the vulnerability, access to the database was restricted after a week. During this time, the number of documents increased from 513,876 to 664,934, reflecting the addition of 151,058 new records.
According to a report by USA Today, Propertyrec is an online platform providing access to millions of public and private property records across all U.S. jurisdictions. The company’s support team confirmed that their services also include criminal background checks, Department of Motor Vehicles (DMV) records, and vital records such as birth and death certificates.
Numerous user reviews suggest that the company advertises the ability to purchase individual documents for as little as $1 per query. However, in practice, customers often find themselves subscribed to recurring monthly services instead of making a one-time purchase.
The background checks were likely conducted without the consent of the individuals being investigated. In the U.S., court records and sex offender registries are generally considered public information. However, aggregating data from multiple sources may have allowed malicious actors to create comprehensive profiles of individuals, including details about their relatives, employers, or acquaintances.
These detailed profiles could be exploited for targeted phishing campaigns or social engineering schemes. Cybercriminals might leverage information about family, employment, or criminal history to extract further sensitive data, including financial information.
This vulnerability comes just months after the data breach involving National Public Data in August 2024. That incident exposed names, addresses, phone numbers, and other sensitive information of millions of users. Hackers infiltrated the company’s systems and posted the stolen data on the dark web. The breach included records of citizens from the U.S., Canada, and the UK. Furthermore, the attackers offered access to National Public Data’s server for $3.5 million.
The discovery of such vulnerabilities underscores the critical importance of stringent cybersecurity practices in protecting sensitive data from unauthorized access and exploitation.


